Credentials used for IT landscape authentication deserve extra attention. Most noteworthy, IT security is today's hot topic. Do not leave open gates to hackers by losing control over your credentials. The following chapters are about the proper management of credentials used by the platform. Ensure continued secure access to devices and services throughout long-term business operation.
Managing the validity of active credentials (changing leaked ones, set of restrictions on their form) is not the only aspect of credentials management. Another important point is the credentials relationship management. It decides the set of valid authentication targets for each credentials item. Choosing the right credentials strategy optimizes network load and computational capacity.
This series of chapters assumes the configuration as performed previously, especially the organization units and devices.
|
Tip: |
Example scenario
These are the credentials we will use in the step-by-step guides. Add them into the system to be prepared sufficiently. Choose the same display name as the username.
•Unix RSA key
Username: UXADMIN
Private key:
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQC0xcewjiQ9B2DD
pD0NiOFJ3joTrf/Bt0bKhF28C7jBbC4ojhOEPn5wzpZj0V9wEQ6f1DA1IXOAk5tD
z1MbN5waG0GNY8L8wusGc6FGs1X1PChntHzkuCu+PLHwaVaxV6FM1vSinwzQntV3
XZ4bupkb9kne6PrbAGTxG3XIdtkJDSv+MlxX9znseeE8J4W9c4ryevqNs6QXrWgP
0ZnXW9myTpKRSp6u30akjlucuS7c79HDb5qn4+OCRFE78pw0CGydKgLkavx9eIcd
wDlnJ02kRV6YrKqucahOBVCZRe/3KqlKk+FH5ESyPhaZtBjMo3fhAZjKkuYkzl+a
Uw0ps9PFAgMBAAECggEAEUSfVFc6UPYby98sJyx/JiOV9VFMEBYmK1bvmUn0Bniu
BBkQ9jNTYrU+mnRioyg4ob3kM6m+syE71gNqUzxBq3YVEfYzUcUmLEHuvaaIkdot
mz0bfRcMCVUaQ6ExsykayGX0N8tCWcoCZtpI2H8/pvMk5VKTZp4oBlFy3okJJxsI
5Ufi3F49DYUg2hZT/Ij61/vyknOsKMD+GNFB8f7IuT34tLrFje0j5Vb+nummsUUE
04hWI72vnfOloFtqz0Am90Rc7tdOIasKv4OMn7ZKkoQECsxJ18+5TXF3RVE128TL
mTbDkRdPonSEE24e3SKZQXNF4mb/PlQLtcWpSdvptQKBgQDbzRNi8Yy7x6ZnDbku
Y9OiSvwxo/en1OaOIoAcGXZvimK2zSHisssroqGpmkHfddhRLez6+4M1PQySTQTZ
5O6bzTH2vIHHI8XB35tWkh7/ioBrPdvFTJ3phh/beLi/KuCj4Nd1ZM6QEafhHfm9
lBAHT+ZsA6EM3av0Iw9PVWGozwKBgQDSiz48y0CoABHul9udxbtb/+LI7IhCQE2q
fGnfbGGkxG3RDRB5OEHijm9xjaqQgbKB/iIzAWZrFdqDygPHkgeVGyEb4KOxROCD
FVk8f5yYtbxzDkB+Dn4Vq5u2heB3tM3GaT5+1vxSlyzjqOttxpOIZDZCXjJnsVjx
ACg7ang3KwKBgH1hVhWyxBy5nmpaoa+csjR5obKPXc4W3A1oELv2qmCmB/lOum2e
n9acRquAmuLlTifAktX4crgDwxARbxr8REALpNyiW0VFWqFk9C9F2vjaALcr6hl5
wvpa0AFZs8kYpFvW/hCxGEOGTsVTXAqQUzRYl5A14cB9EoGJHkqa4cJxAoGBAL7d
Ed+k1gk2fwsPSTz+qnmdP+arXl7I0l9yB7xOETqAA5mWwU9Sq4+JVgfXyD7WBJAJ
ZNFePI1pMz1znfeGLy+Bd4NBIsOpz+mlKc9JVBmv7pVS3y4nTy+v8SoGtVVvZ3et
osTzeawZdc0wLbTHZqknR3Tk1cbgo+NeJBqwyygfAoGBAKp9I2uFR2wjMaLv5XKs
EuEI2k9Y5ArnFnSqwdzGNwAQKIn9gWtlYf/GFrIMt9apELzrx+49hYadFFSnLtdH
Hl/NxO8cSOr9dAyIGpcZhmqJyULlMeDSvI9Kr2JNrI2Xwy9Eji3S+eBTR5AX6aic
l/YNsB2tHEuvdRRDuZHke+3o
-----END PRIVATE KEY-----
•Unix ECDSA key
Username: DEV01
Private key:
-----BEGIN PRIVATE KEY-----
MIG2AgEAMBAGByqGSM49AgEGBSuBBAAiBIGeMIGbAgEBBDAKsvAlZg//+FVVSp4h
IvzzGrnCJTqcvGE0blOzu0BgoWtpbxB43kwrEcd+iHWeZWGhZANiAAT4Wat9sS7m
U9EFmHTmDI815ZFzH8y7+mySb82okUvYTGEJnd7+KLTdEN/7qXPBFs7yfMyf+BOc
pcdjb3FaTDJ4OOwPGmZbHOTRv2qE4ikX1iFQLyvn5r+plEXRtd2zX+s=
-----END PRIVATE KEY-----
•Unix plaintext
Username: www-data
Password: ia64
•Windows plaintext
Username: CONTOSO\Administrator
Password: win32
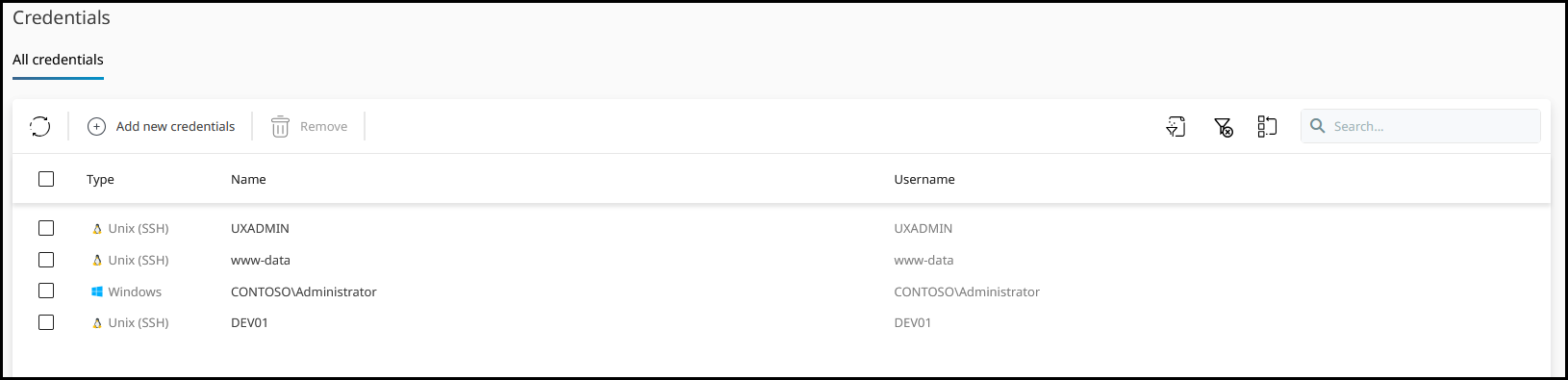
This is how the list of credentials should look like after adding all the credentials to the platform.
device-credentials relationships
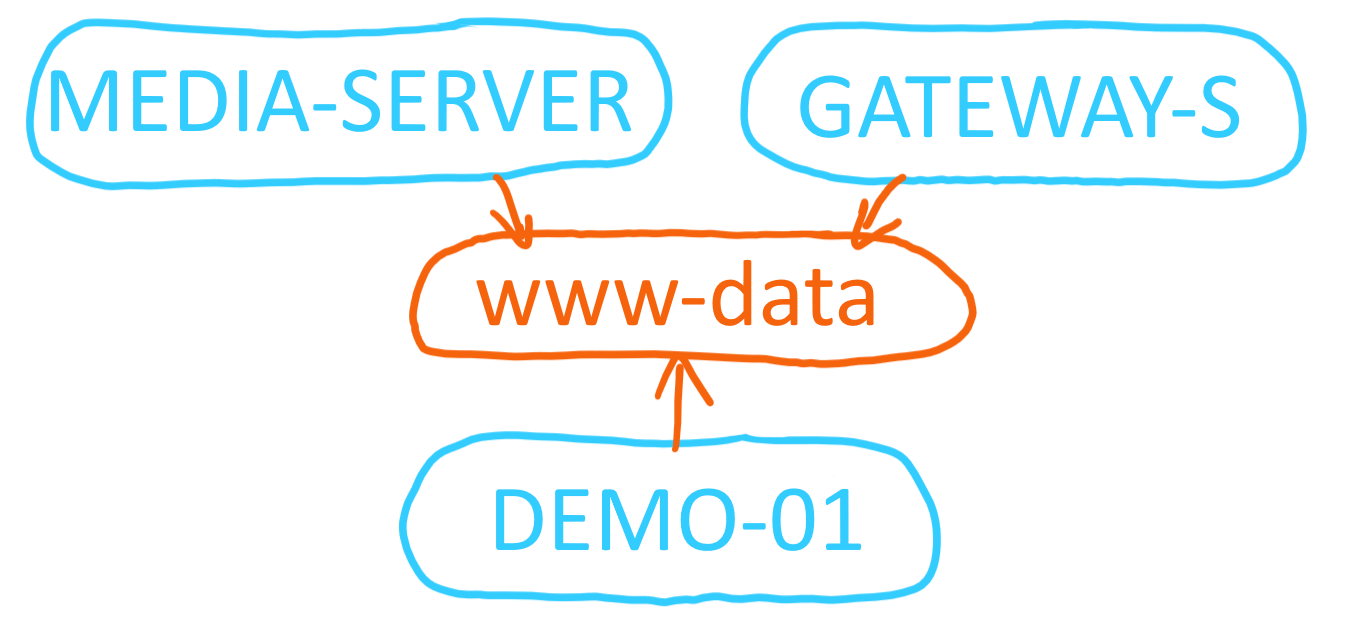
The www-data credentials are used by three devices: MEDIA-SERVER, GATEWAY-S and DEMO-01.
network-credentials relationships
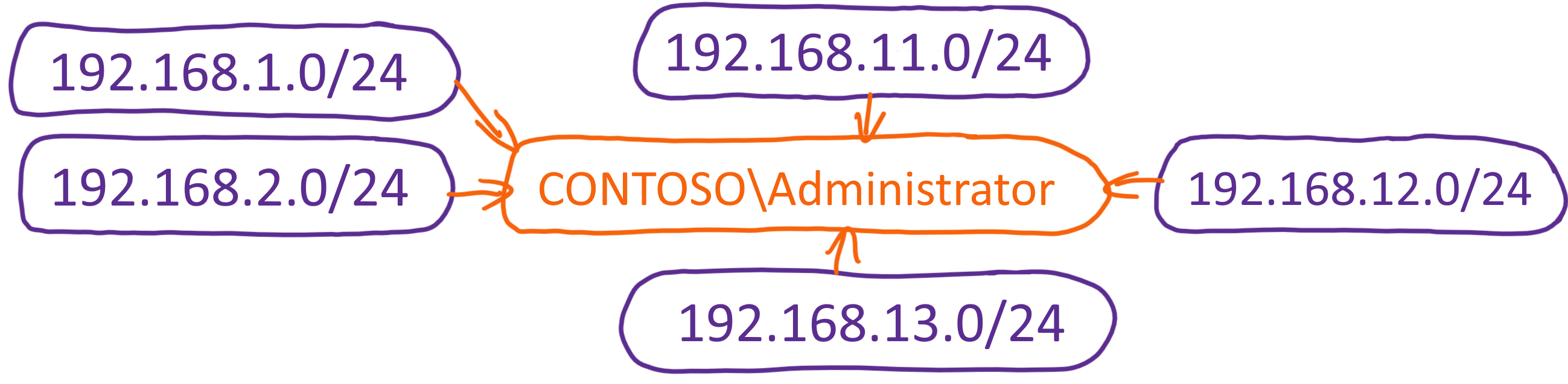
The CONTOSO\Administrator credentials are used by five network definitions: 192.168.1.0/24, 192.168.2.0/24, 192.168.11.0/24, 192.168.12.0/24 and 192.168.13.0/24 .
site-credentials relationships
The UXADMIN credentials are used by two sites: Default Site and External Site.
OU-credentials relationships
The DEV01 credentials are used by two organization units: IT PB and IT Ibl.
Supported credential types
Plaintext credentials are commonly used. Due to their simplicity and historical developments of the IT industry, this form of credentials is the most widespread one. But being widespread does not equal to being the best choice. When used in combination with secure protocols like HTTPS, they are protected against snooping along the way of network transport. Usually, they are transformed into a username and hashcode equivalent credentials pair to protect the distinct nature of the password, introducing security-by-ambiguity per one-to-many mathematical function. Although, an effective attack means is to hijack the device routing, for example by directing the authenticating party to credentials collecting stub servers. Unfortunately, as easy as they are to construct, this form of credentials is vulnerable.
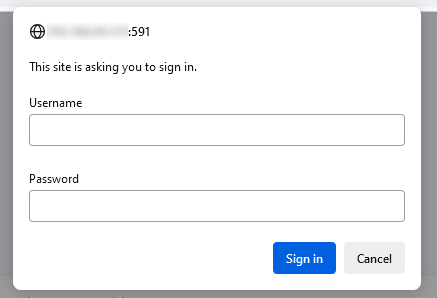
Input form shown when connecting to HTTP web servers which require basic authentication. The moment you are faced with such an input form, you should ask yourself whether you trust the safe handling and processing of your plaintext credentials. Plaintext credentials in the wrong hands can cause big damage. Thus, if IT security is dear to you, choose mathematical-challenge-based authentication instead.
Public-private asymmetric cryptographic key-pairs are a strong means of authentication. Its strength roots in the solution of difficult mathematical problems. The larger the ambiguity by amount of solution-attempts, the stronger the mathematical problem. Popular strong cryptography is labeled RSA or based on elliptic curves. When the mathematical parameters are chosen right, this credential type is much stronger than plaintext credentials. Various services exist which recommend you the proper cryptographic parameters and build the final form of credentials for you (tools, web services). It is important to generate the cryptographic parameters on secure grounds to prevent leaking them (local device, transport via optical disk, temporarily detached storage media, secure cryptographic circuitry/chip). Choosing this asymmetric cryptographic authentication strategy requires greater, albeit not monstrous computational power.
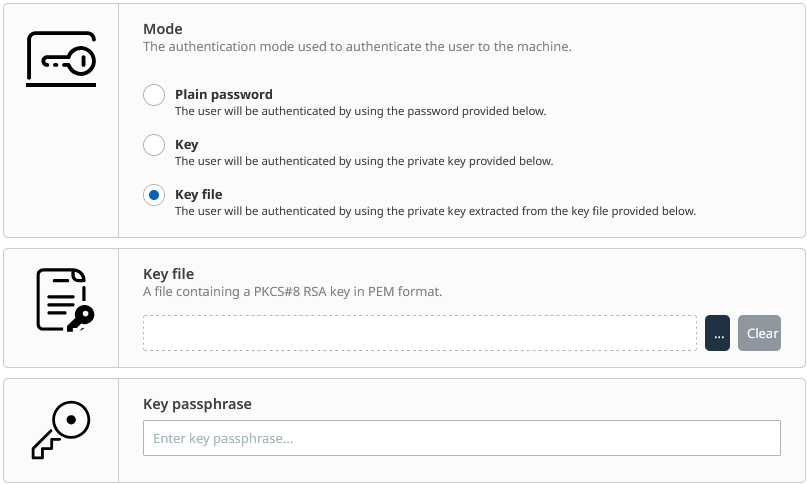
Cryptographic key-pair input controls accessible as part of Unix credentials addition. You are expected to provide the private key to use in Secure Shell (SSH) authentication. It can be provided either via input text-box (the option labeled Key) or file located inside of your device's filesystem (the option labeled Key file). If your screen is publicly watched, prefer to provide the key by file.