Raynet One was designed to provide you with IT Visibility over your assets. However, efficient IT management does require a safe and healthy environment. The platform has got you covered with capable tools. Additionally, the platform itself supports various troubleshooting means, e.g. analysis of failed inventory or discovery runs. Learn about IT landscape maintenance by reading the following chapters.
About IT landscape maintenance
To maintain the IT landscape, you should find out about software vulnerabilities and errors across your assets, or even platform operation. This topic is not to be confused with organization, covered in the previous set of chapters, to keep things working by design. The platform provides you with rich information to inspire you for solution crafting. In certain critical areas, you will read about recommended troubleshooting. The most bare-bone approach is to inspect feedback (log entries) from running solutions (platform instruments, device software, network nodes).
Software, in general, is known to break no matter how good its reputation is. The surfaced flaws are related to technical limitations, evidential design flaws and aging IT infrastructure. Due to the scientific complexity, there doesn't exist a single button to solve every problem automatically. But insights provided by the platform aim to be helpful.
In today's rapidly evolving IT world full of unchecked or intelligent contributions, the Technology Catalog aims to provide access to blaming and monitoring knowledge networks (CVE, CWE, vendor security feeds and software project issue trackers). Be on the fast track to (supposed) technical decision makers and stakeholders. Influence the product's reputation (factored by quality, score and public reliance).
Known product flaws, such as offered by the platform's vulnerabilities view, motivate the product's replacement by update, complete substitution or evaluating alternative solutions.
Raynet One's intention is to provide actionable intelligence in comfortable form. In terms of vulnerability, you are empowered to investigate the relationship to real IT landscape resources. Observe the vulnerability profile caused by (employee) use. Evaluate the IT landscape by vulnerability score and device (internet) exposure.
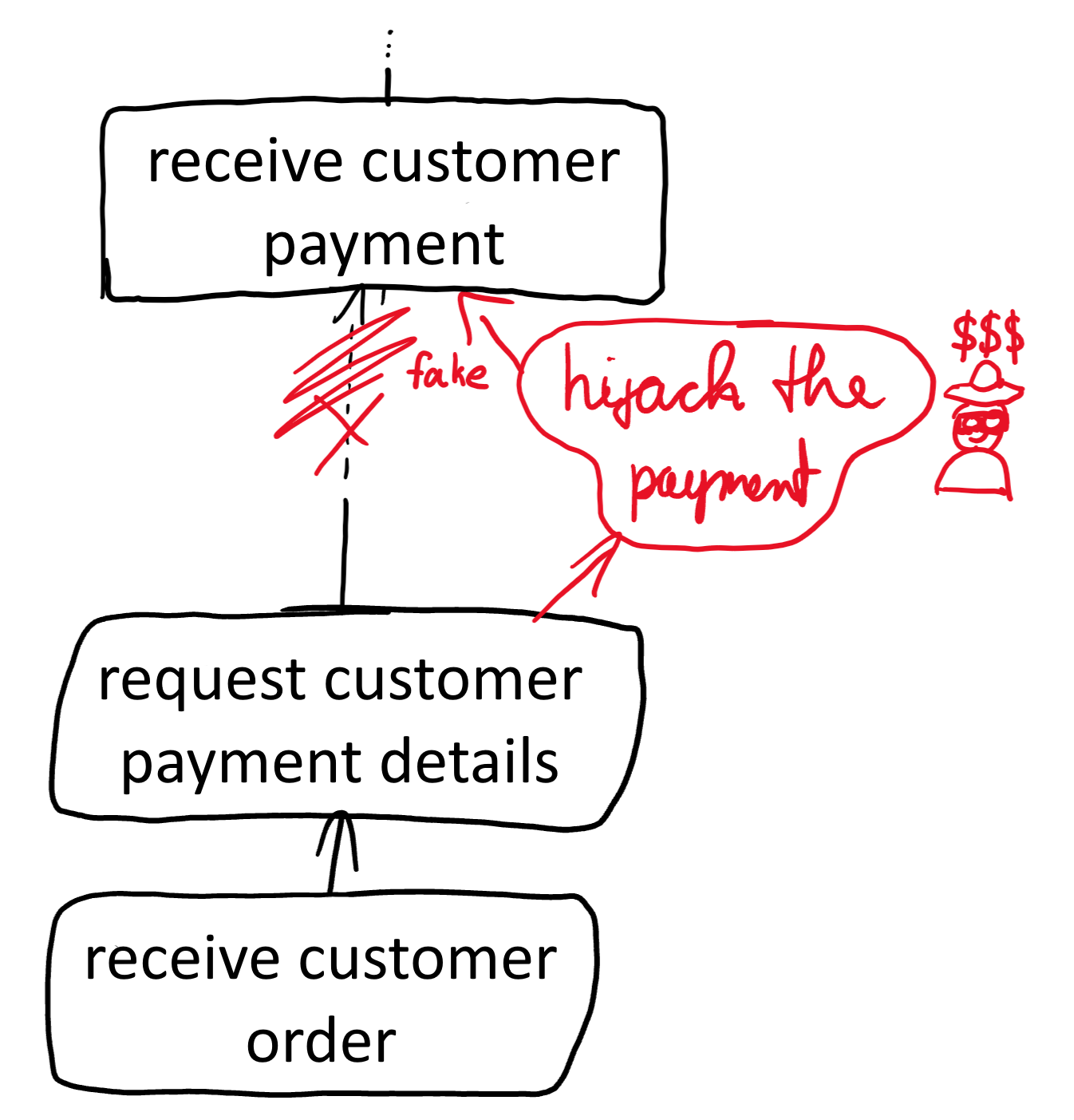
Excerpt of a typical business ordering process hijacked by an attacker. The attacker has hooked the next step of the customer payment details request. He aims to receive the details himself in order to hijack the payment. By exploiting vulnerabilities, both technical and social, attackers can modify well-established corporate work-flows using hooks. A well versed scammer knows how to fake the confirmatory process even after the hijacked step. Modern human language interpretation solutions (AI) allow machine-powered hijacking of human interfaces plausibly (video or telephone calls, chat). The possible damage depends on the grade of permission the vulnerability can expose. Learn about technical phrasing related to vulnerability risks to properly understand how specific vulnerabilities could affect you.
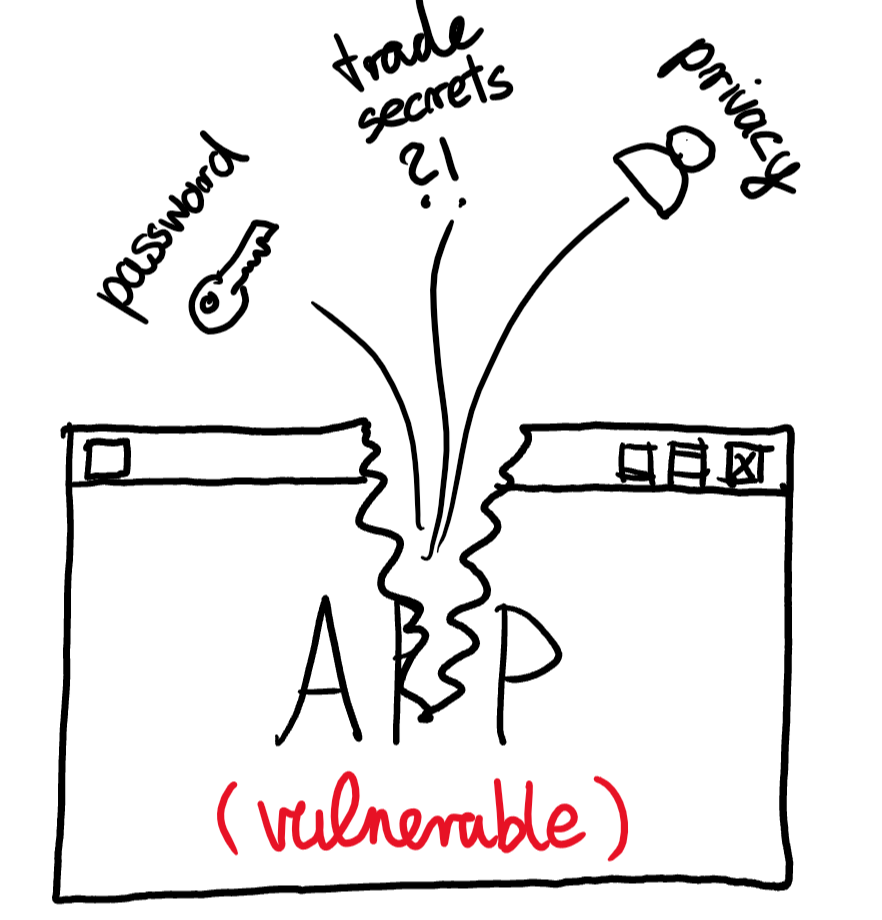
Illustration of a torn-open application by vulnerability, leaking various information. Vulnerable applications can expose critical information to attackers such as passwords, trade secrets and privacy. That is why keeping an eye on application vulnerability is so important. Every business has to stay vigilant due to uncontrollable change and trust in today's IT world. Applications deemed safe today can turn into RAT gateways tomorrow. Is it really worth it to merely skim over and past, rather than take IT security into your own hands?