IT security is key for well-performing and safe IT landscapes. So, logically, outdated software or hardware (EoS and EoL) as well as so-called Shadow IT (individually installed software from the internet, even open source) harbors the potential for security gaps, leading to a vulnerable IT landscape. Use the Vulnerabilities overview get a full summary of vulnerabilities detected in your managed environment.
The view also displays a standardized vulnerability score numbered from 1 to 10, in different colors, suggesting the urgency to take action. Generally, red or orange state items with values between 7 and 10 demand attention, security investigation and sometimes even changes in the software portfolio. Never fall behind on the topic of secure software planning.
Publicly exposed security vulnerabilities are both a blessing and a curse. Fail to see the vulnerabilities lurking in your environment and let the motivated hacker use them to get inside. But take the security bulletins seriously to stay up-to-date security-wise. Due to the different response times of IT management, it is a race against the bad actors.
To summarize, via Vulnerabilities you can:
•check on existent vulnerabilities and security gaps in your IT landscape in order to estimate your IT security status,
•find detailed information on individual vulnerability sources in order to derive solutions, and
•view and explore devices where vulnerable software packages are installed on.
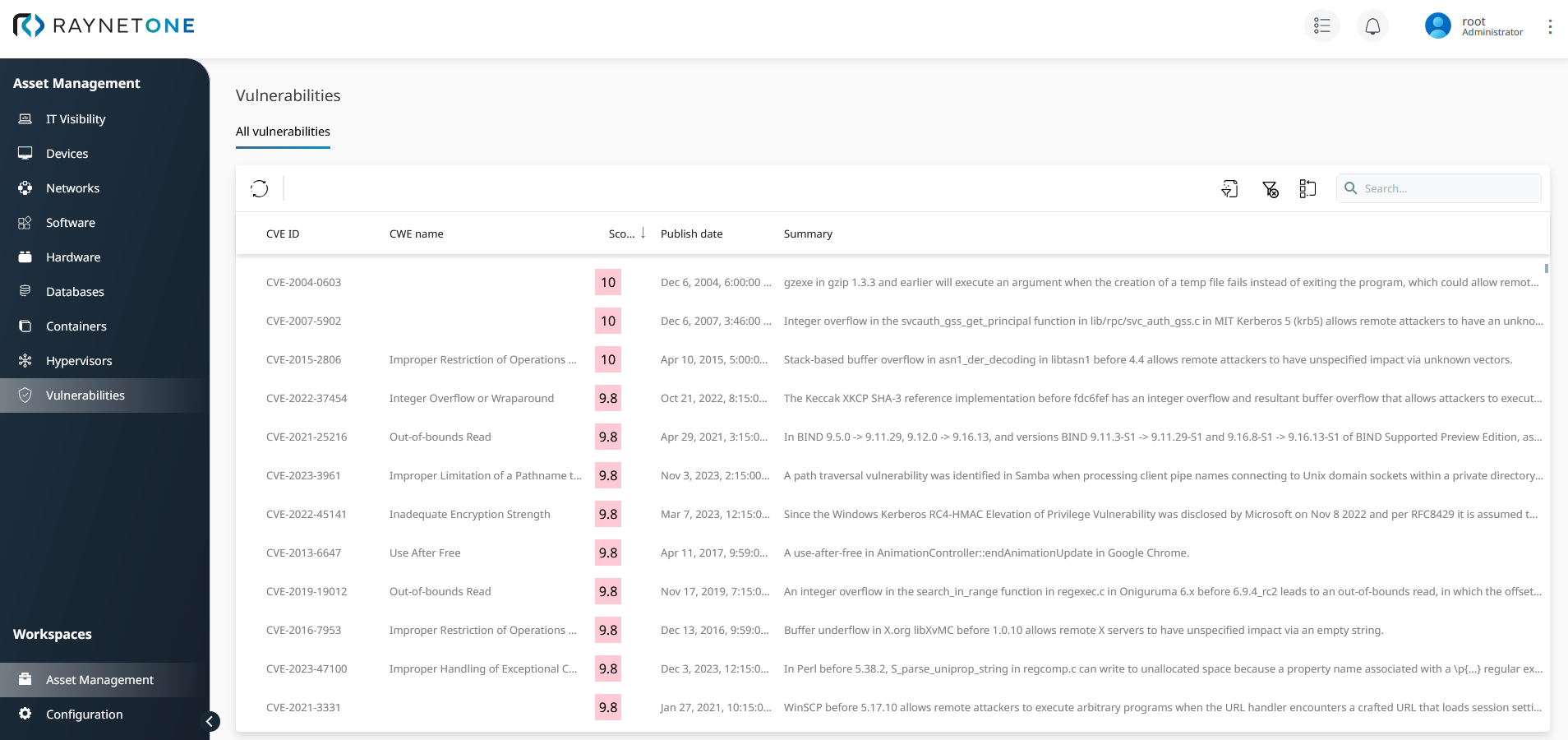
The main Vulnerabilities overview with listed vulnerabilities of the inventoried IT landscape. It is sorted descending by the vulnerability score, giving you the most dangerous security issues at the very top. A helpful summary is given for each list entry, taken straight from official sources.
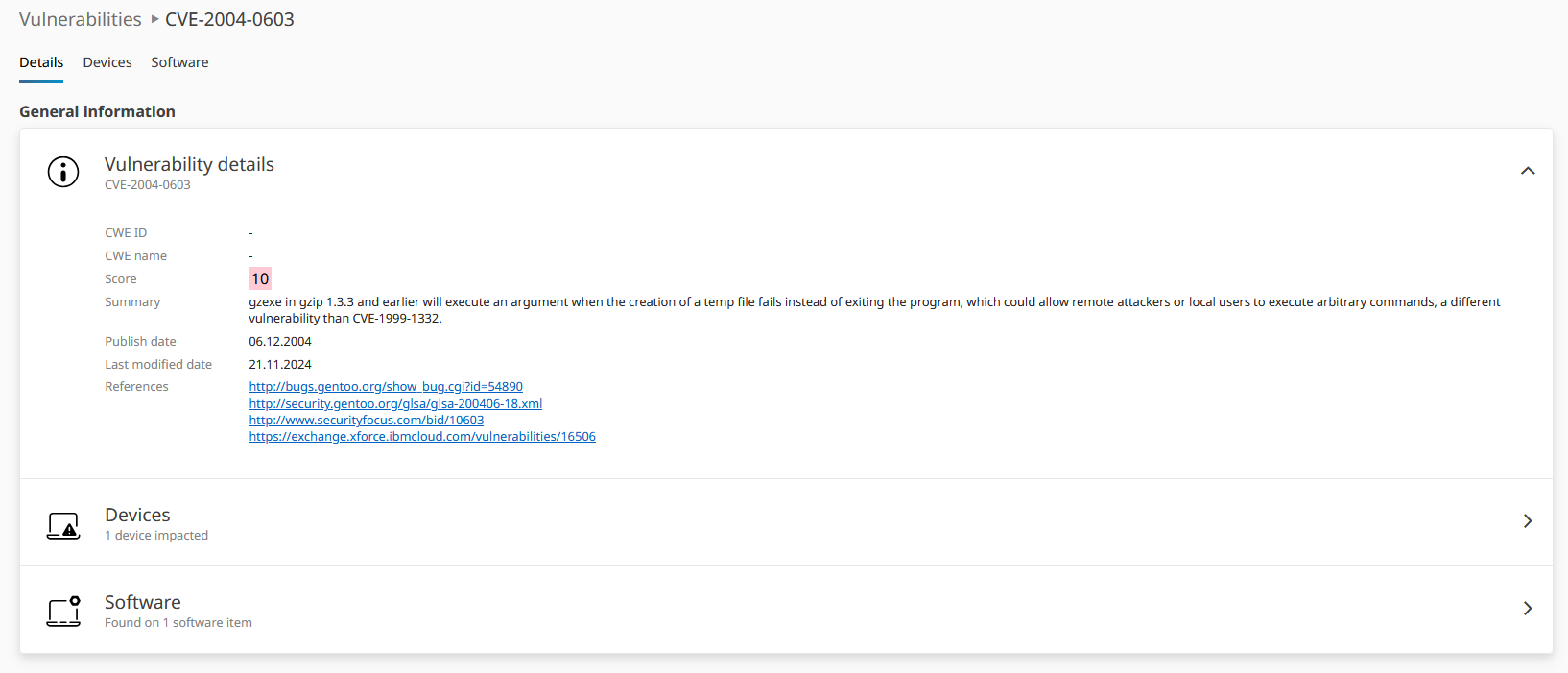
Details view of individual vulnerability displaying the source of potential security issues related to a specific software package installed in your IT landscape. Use the listed references to investigate the impact of this vulnerability on your individual environment and how to mitigate it. Switch to either the impacted devices or the software to see the vulnerability's scope.
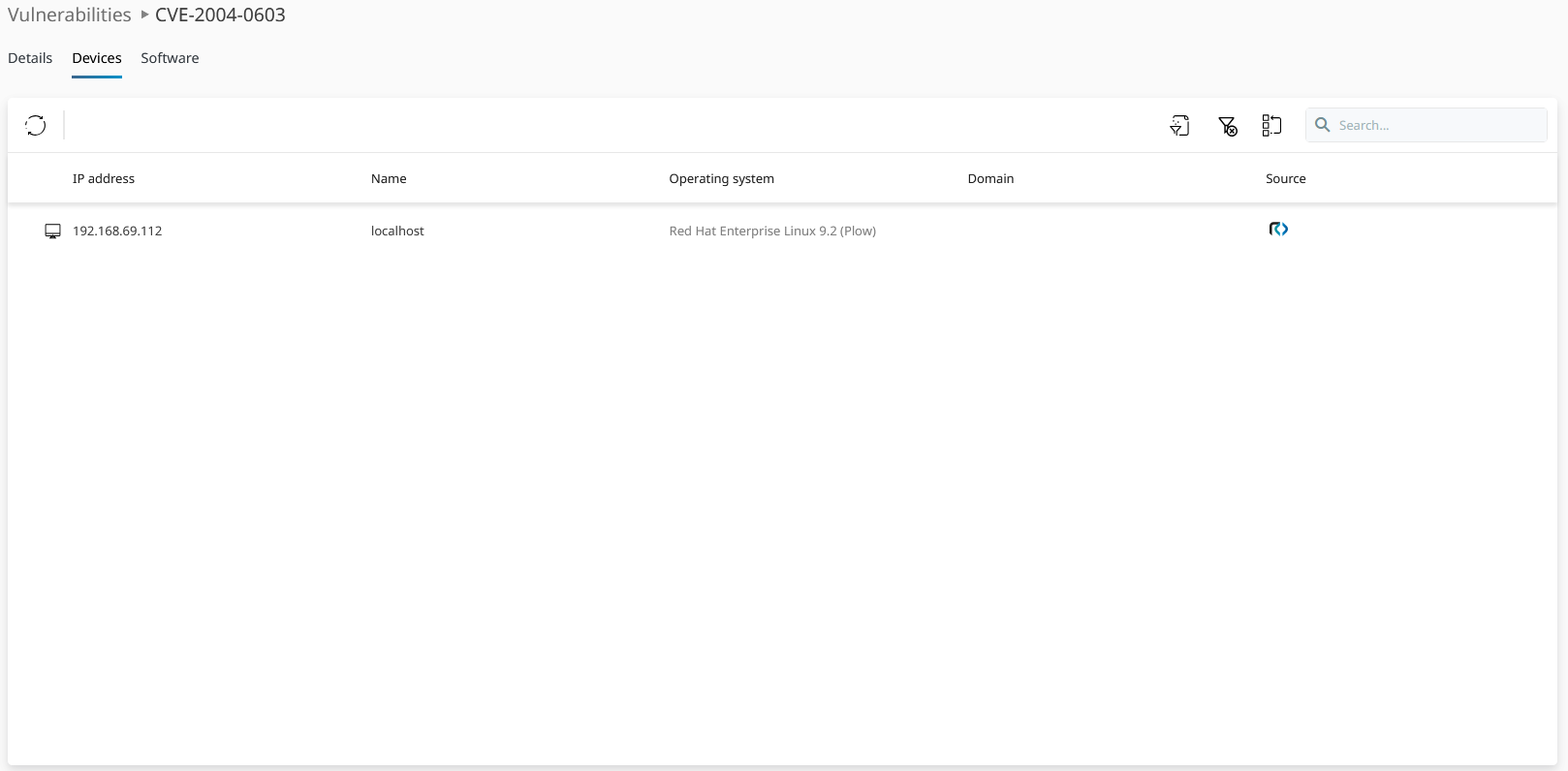
List of devices which a vulnerable software package is installed on, under the Devices tab. In the worst case, these devices are entryways for well-equipped hackers into your IT landscape. A serious hacker uses the latest collection of vulnerabilities to hijack your systems.
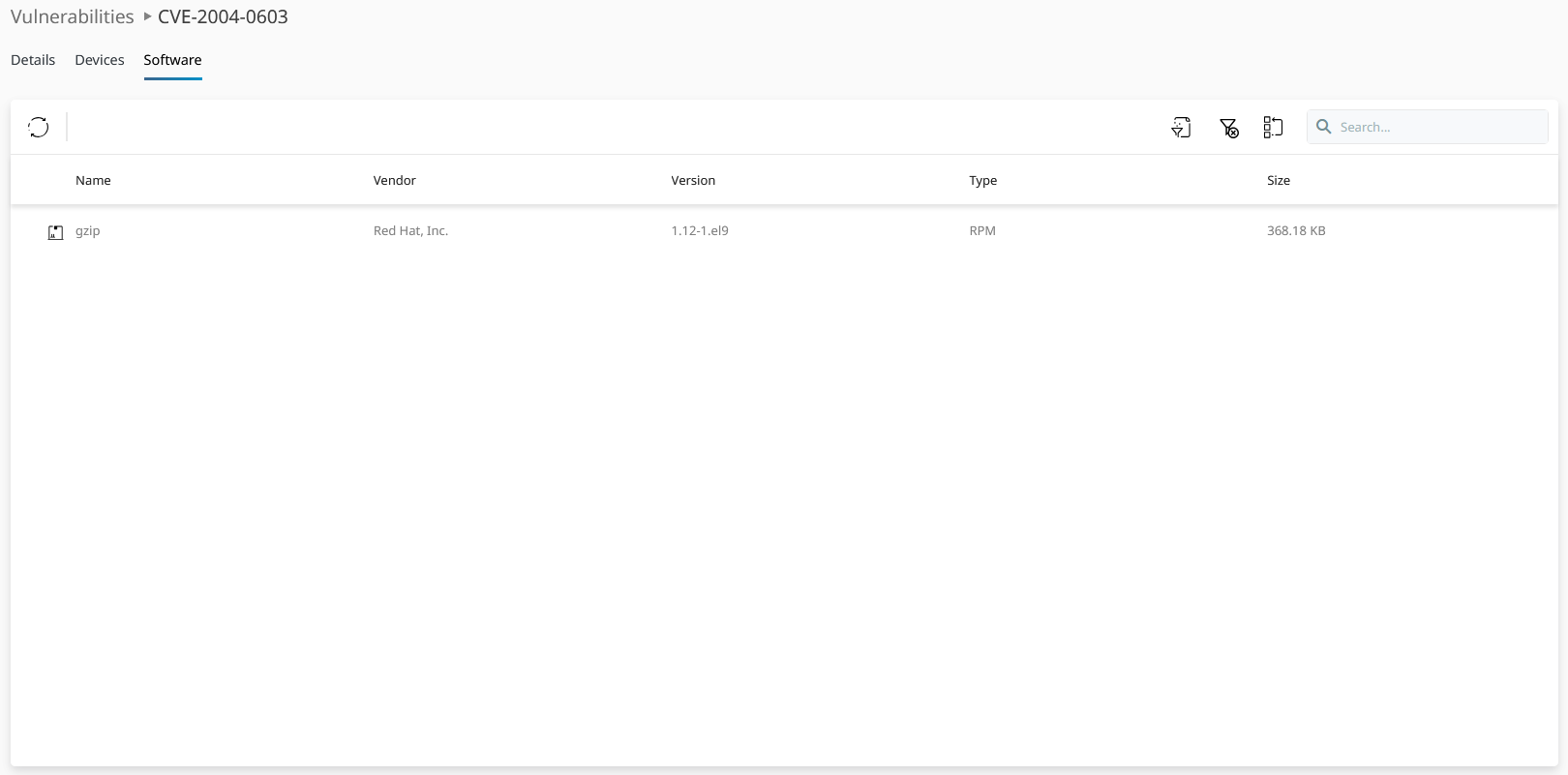
List of vulnerable software packages which are affected by an individual vulnerability issue from the overview list. Note the software version as vulnerabilities can be fixed in a newer one.
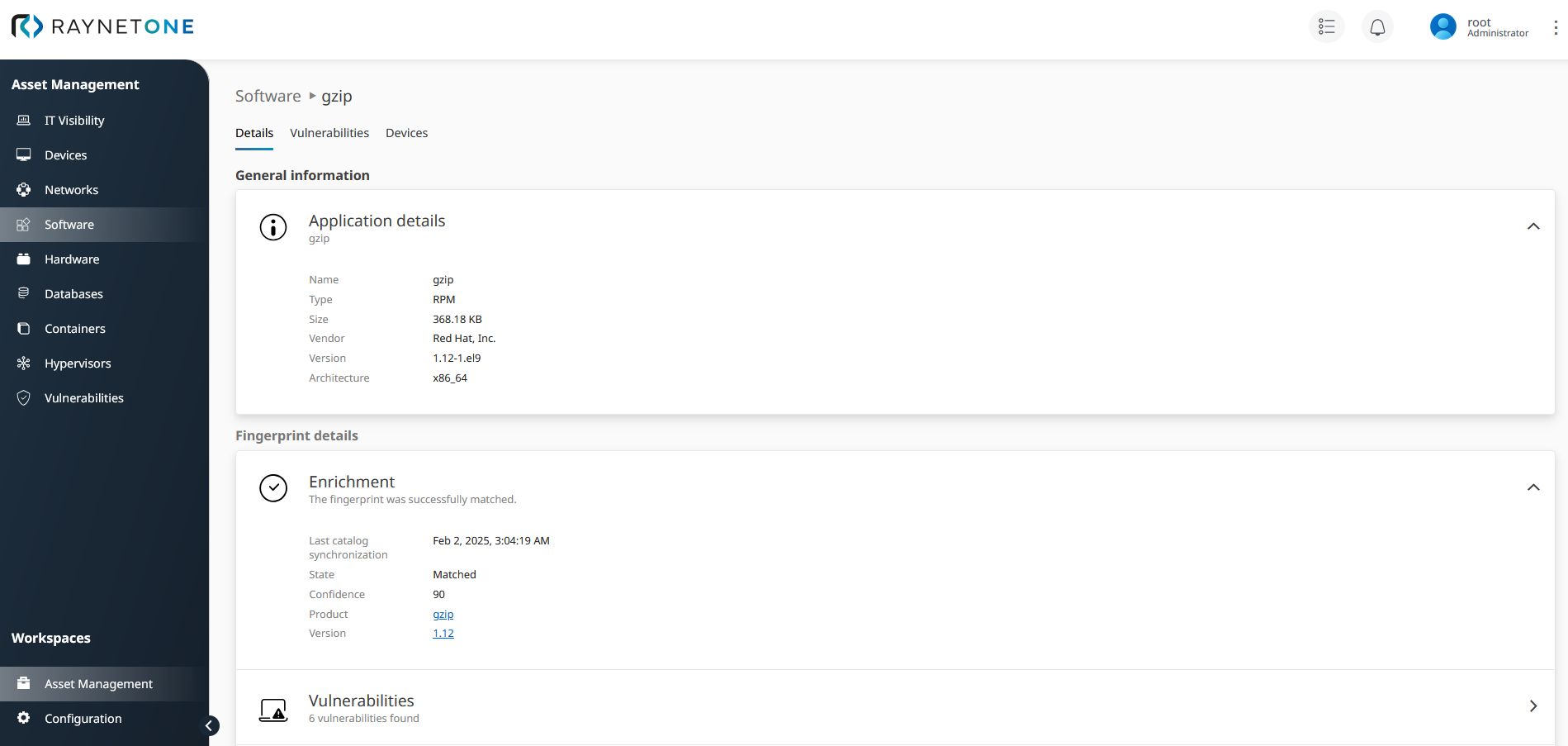
A vulnerable software package called gzip, version 1.12-1.el9. Click on the vulnerable software entries of the specific vulnerability details view to open this view. This software has more than one vulnerability. Find out about all of the other vulnerabilities tied to it.