RayVentory Data Hub supports data encryption of the following information:
•Sensitive data belonging to tasks, including:
oconnection strings,
opassword,
ologins,
oclient secrets,
otokens
oetc.
•Reporting data
The encryption of the former is using tenant-specific keys. The encryption of the latter relies on Microsoft SQL Server Always Encrypted functionality. It makes sure that the data in the SQL tables is scrambled and obfuscated (on cell basis), but the users who have access to the correct tenant see the actual data, both in reports and during the designing. Always Encrypted is a feature designed to protect sensitive data stored in SQL Server databases. It provides an extra separation level between the owner of the data (capable of writing and reading to it) and the maintainer (who should not be able to decipher the content). The encryption key are managed by RayVentory Data Hub and never revealed to the SQL Server. This means, that in case of a compromised database with sensitive data, the attacked is unable to decrypt it.
|
Note: Data encryption is only supported by SQL Server Enterprise. It may not be supported on all editions and versions of SQL Server. Make sure that the underlying database engine supports it, before activating the function. |
Data encryption is not enabled by default. In order to enable it, locate the tenant to be secured, and press Edit to open the edit dialog. The dialog has several options, the one relevant for data encryption is the following checkbox:
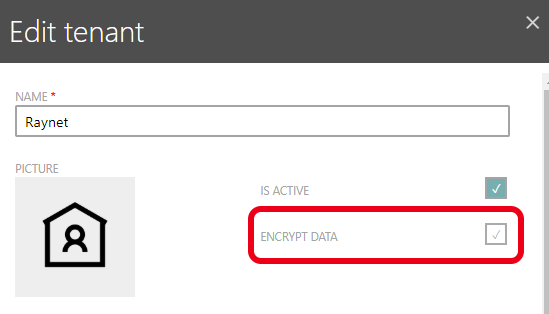
Once the setting is active, the set-up is done and the data is protected.
|
Note: Data encryption adds extra security, but not without costs. It is expected that querying, filtering, sorting and other SQL operations may get a performance hit, due to the fact that every affected cell, column and row must be decrypted before displaying, sometimes requiring extra steps or round-trips. The impact on the performance depends on the amount of the data, the level of the optimization of particular reports, and on the hardware on which the host is running. |