IT security is key for well-performing and safe IT landscape. So, logically, outdated software or hardware (EoS and EoL) as well as so-called shadow IT (individually installed software from the internet, open source) potentially brings along security gaps. This is why under Vulnerabilities, you get a full summary of vulnerabilities detected in your managed environment.
The view also displays a standardized vulnerability score numbered from 1 to 10 and in different colors suggesting the urgency of taking action. Generally, red or orange state items with values between 7 and 10 usually demand attention, security investigation and sometimes even changes in the software portfolio.
Via Vulnerabilities you can further:
•check on existent vulnerabilities and security gaps in your IT landscape in order to estimate your IT security status,
•find detailed information on individual vulnerability sources in order to derive solutions,
•view and explore devices where vulnerable software packages are installed on.
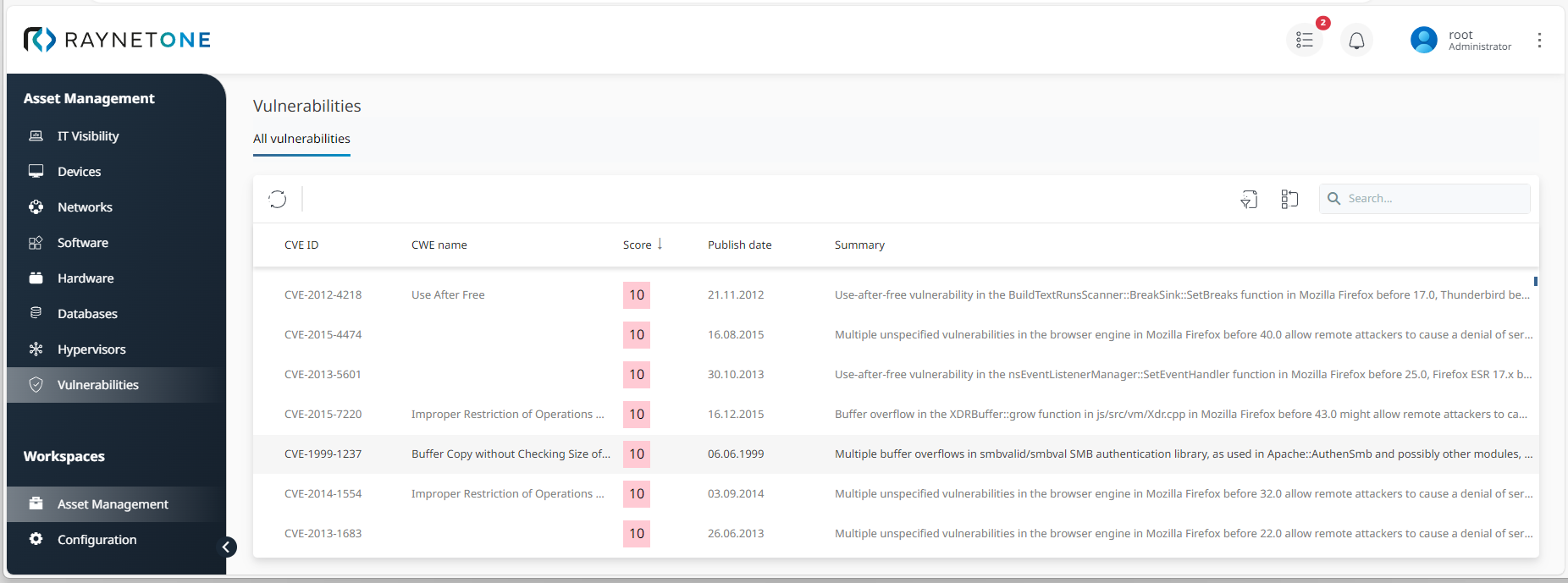
Vulnerabilities overview with list items
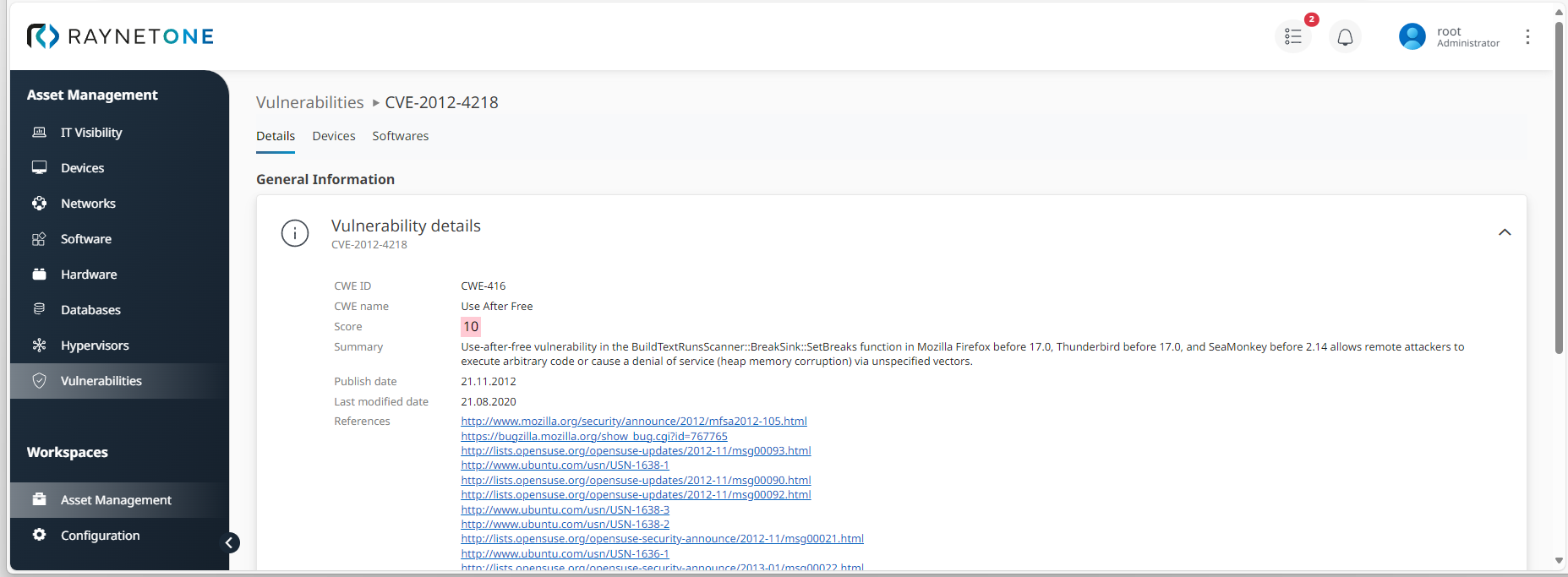
Details view of individual list item displaying the sources of potential security issues related to a specific software package installed in your IT landscape
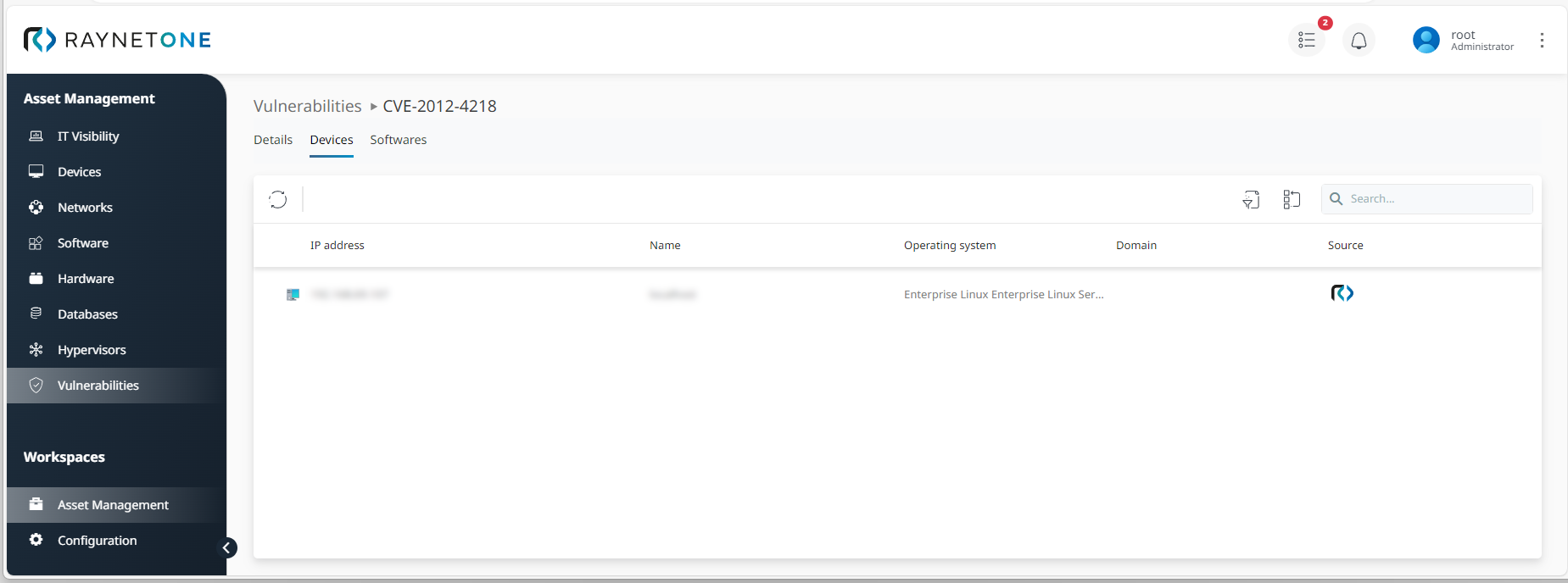
List of devices which a vulnerable software package is installed on under the Devices tab
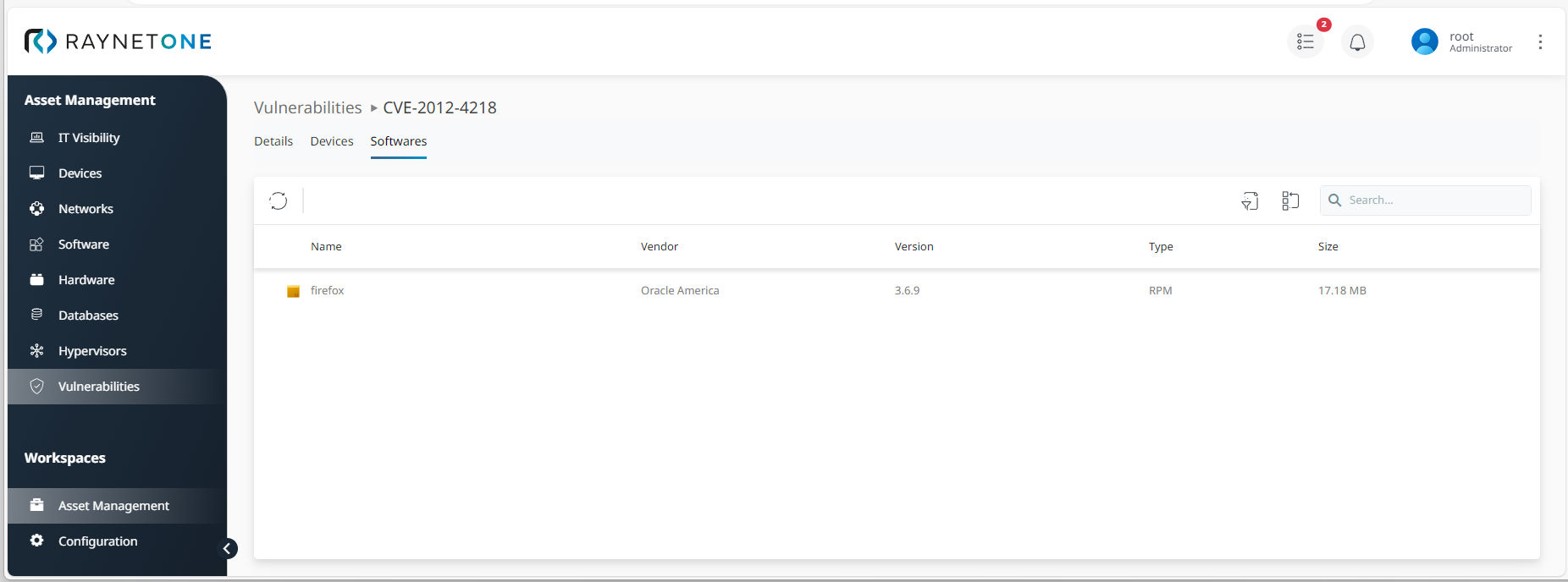
List of vulnerable software packages which are affected by an individual vulnerability issue from the overview list
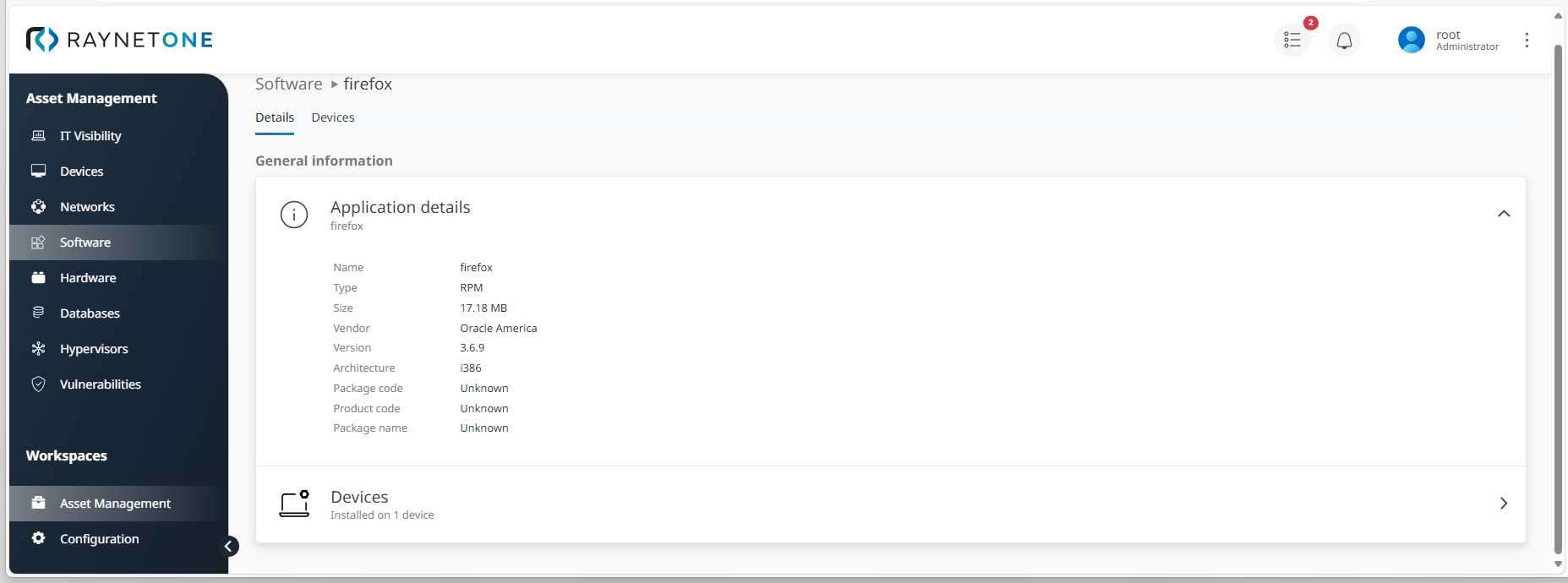
General application details on a software package which is affected by specific vulnerability issue, to be accessed under the Software tab