Whenever you want to monitor your IT landscape's health and efficiency at a quick glance, the IT Visibility dashboard is a go-to view. The same principle counts for IT security and vulnerability issues. So here's how to gain insights into your environment's "weak points" as a crucial part of your IT Visibility strategy.
1.Navigate to the IT Visibility view. It is located in the Sidebar menu in the Asset Management workspace. With regard to vulnerability management, the dashboard includes five main sectors: Overview, Software, Hardware, Security and Gap identification. Please note that all following steps are optional and that you can always change their chronology.
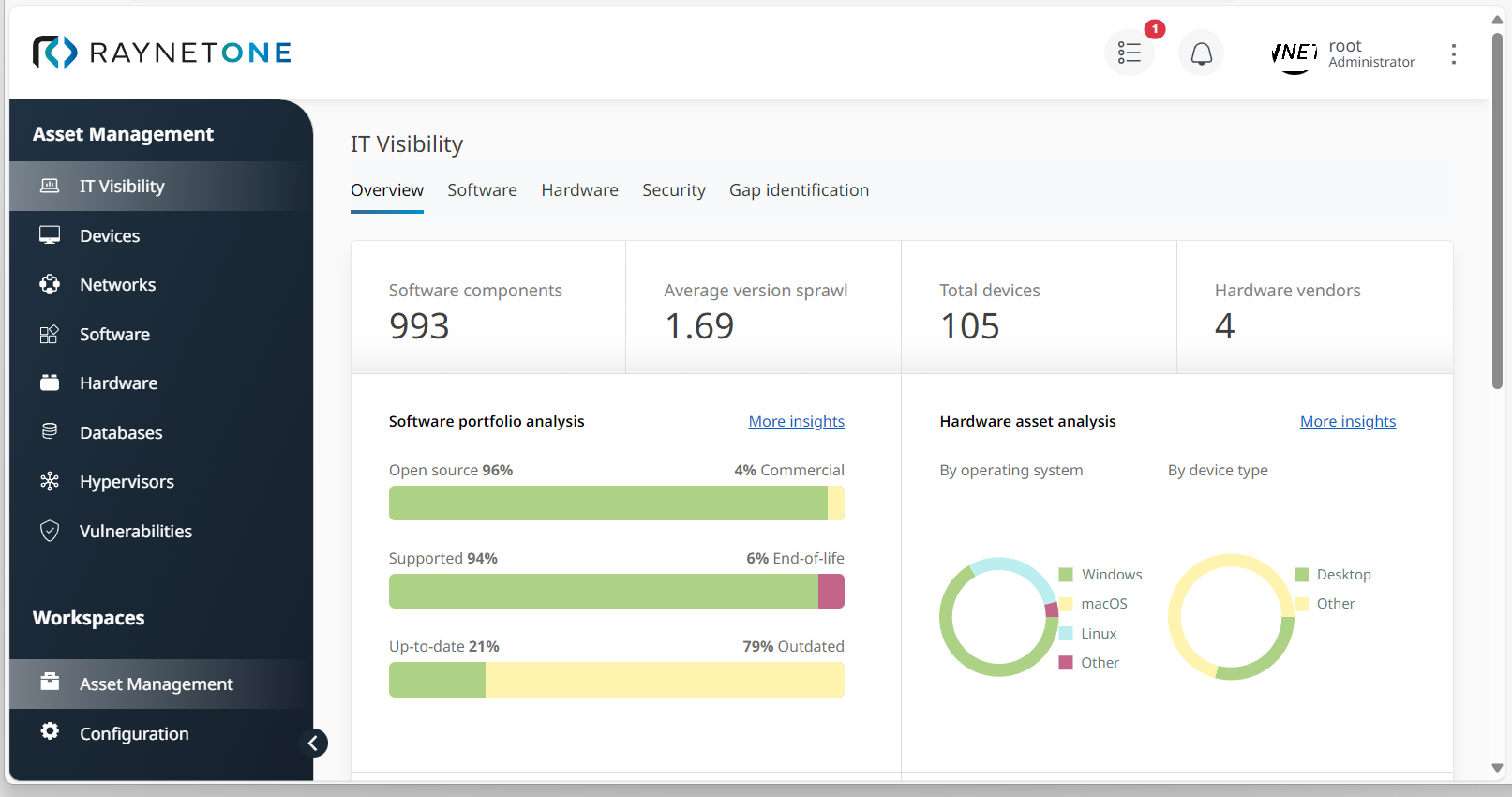
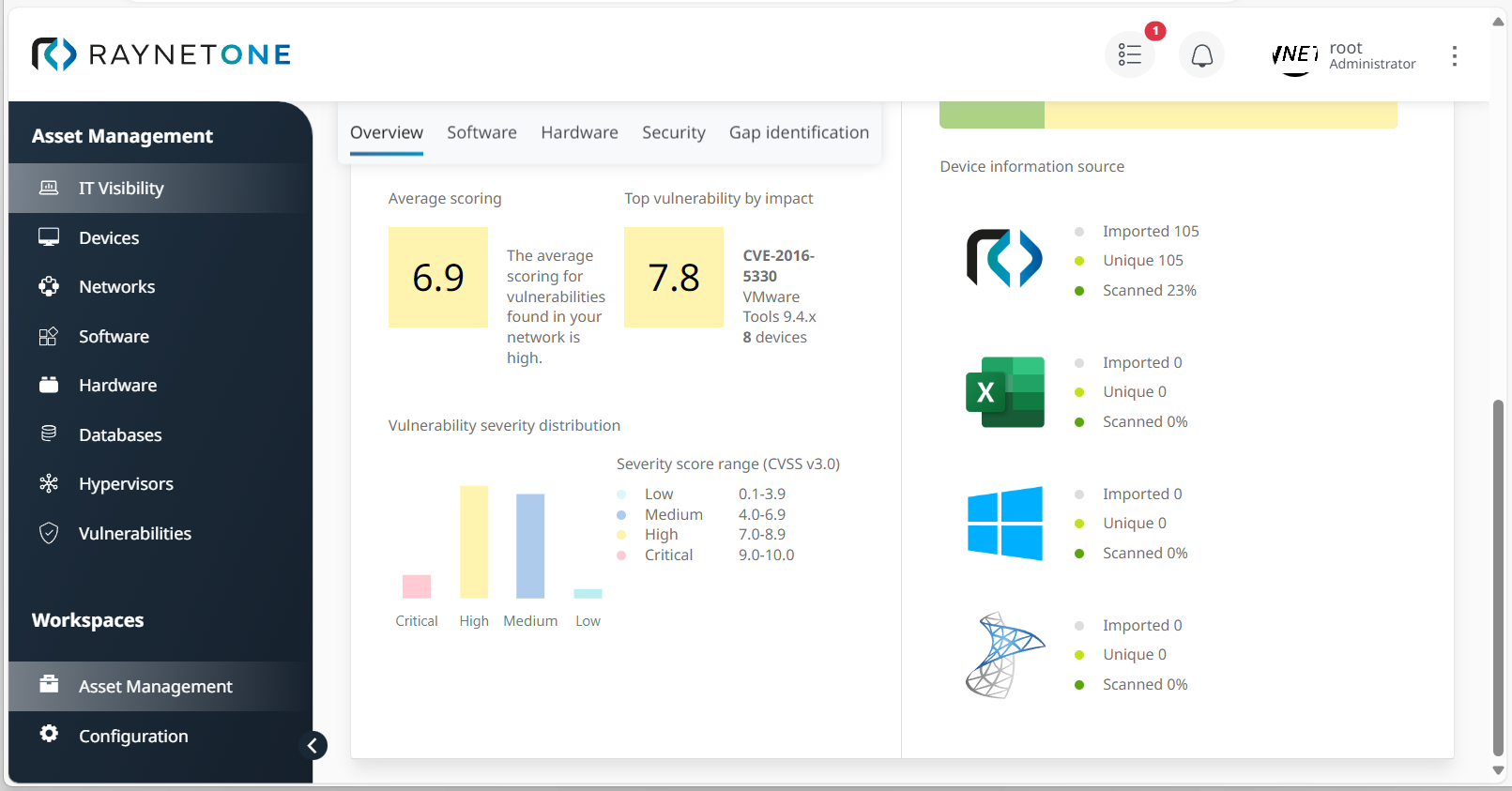
2.Under Overview, take a look at the sector Software portfolio analysis which informs you about the percentage of outdated and non-supported software assets. Also check the current CVE scores at the bottom of the view. You'll find this information under Average scoring, Top vulnerability by impact and Vulnerability severity distribution.
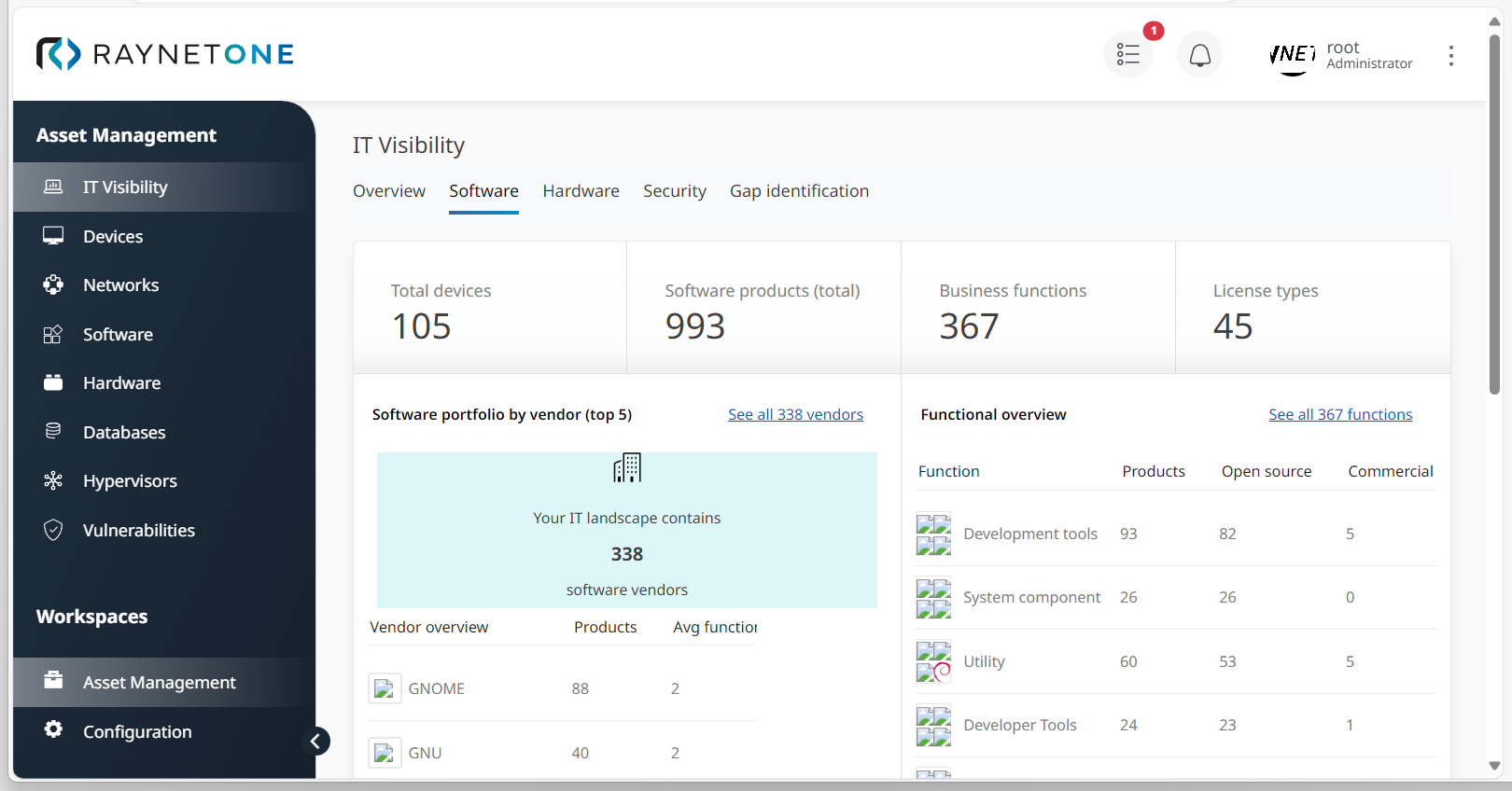
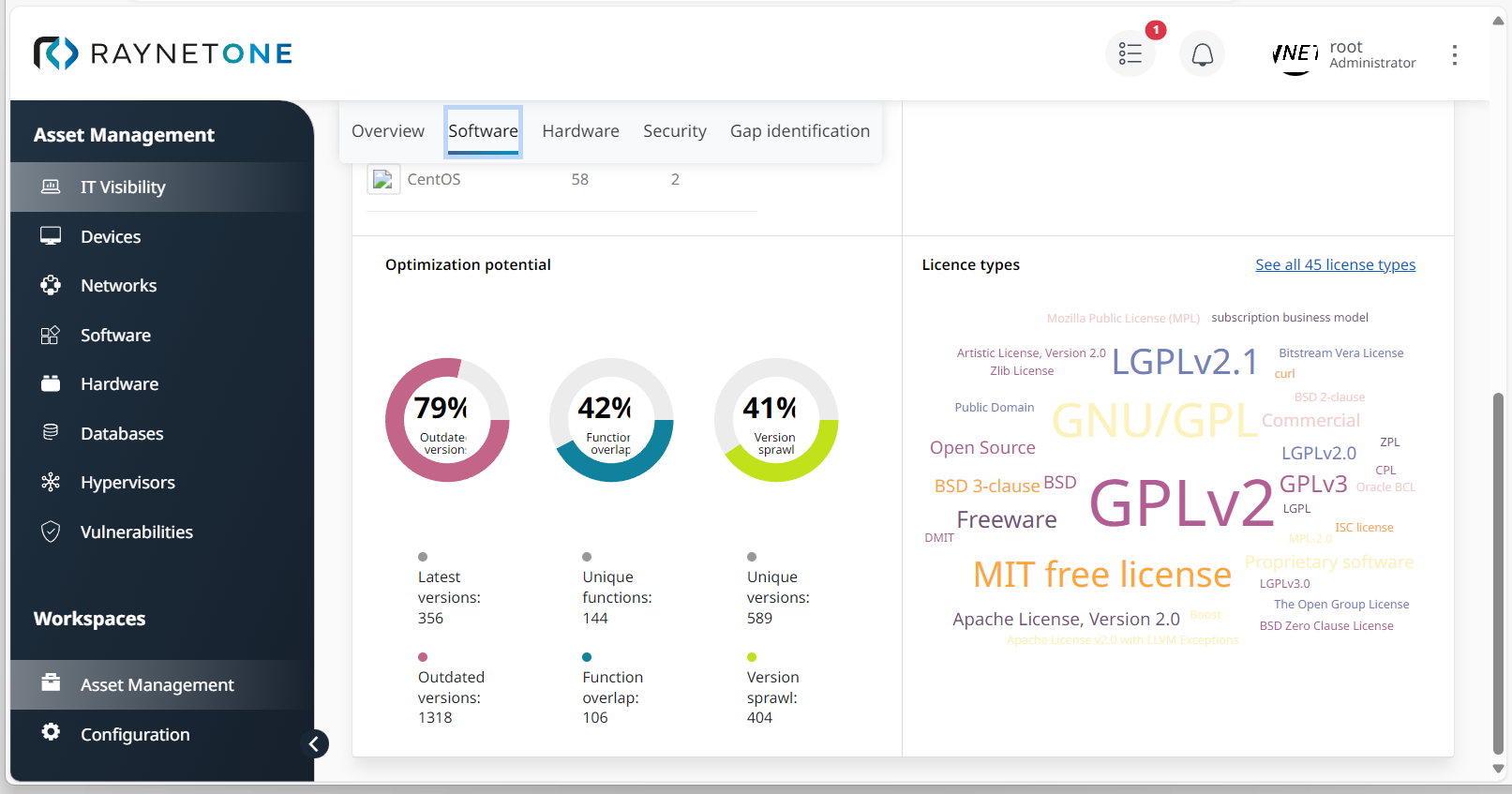
3.Click on Software to monitor the current percentage of outdated or non-supported software versions. This information is available under Optimization potential.
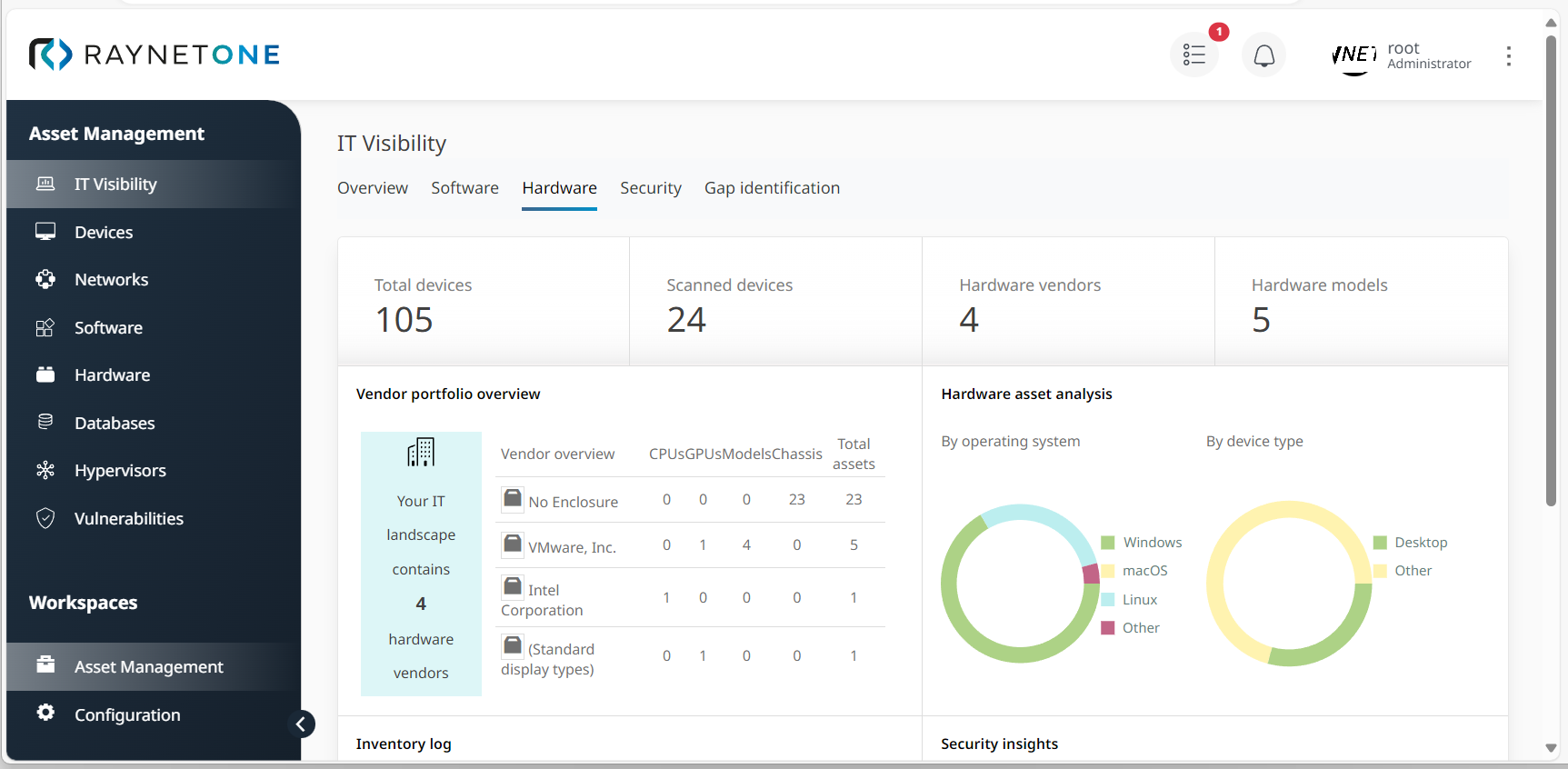
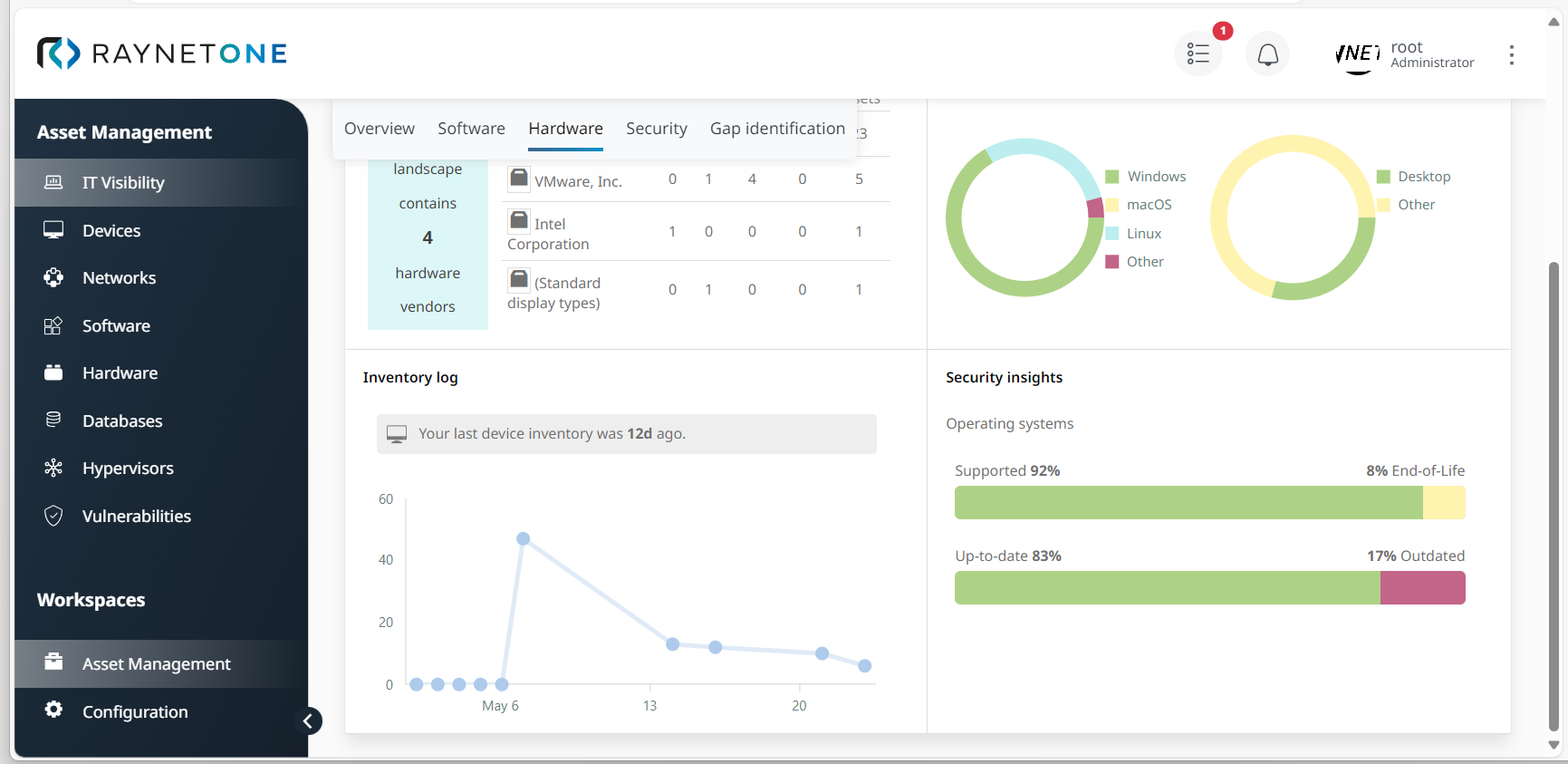
4.Click on Hardware to monitor the current percentage of outdated or non-supported operating systems. You can view this information under Security insights.
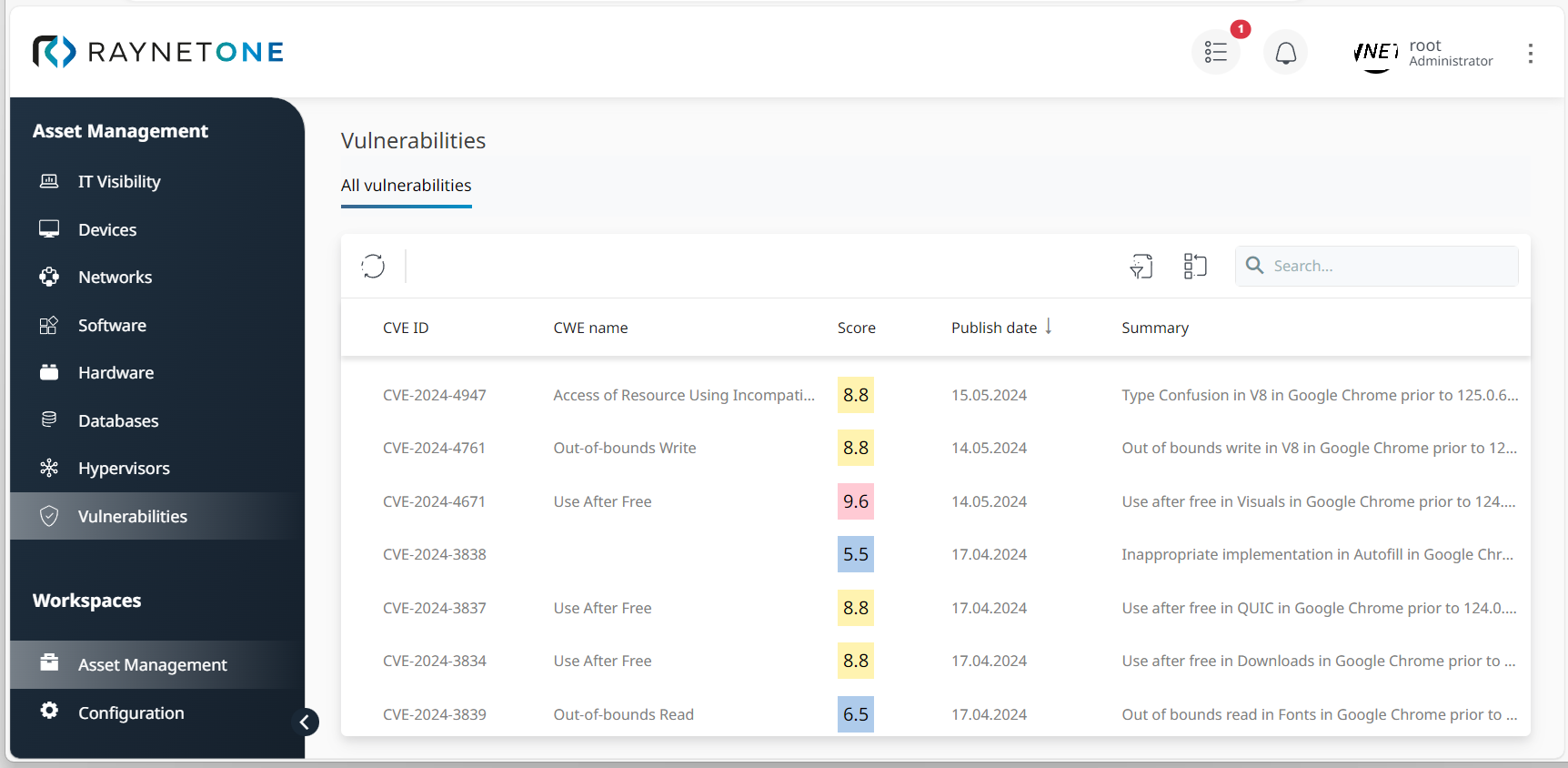
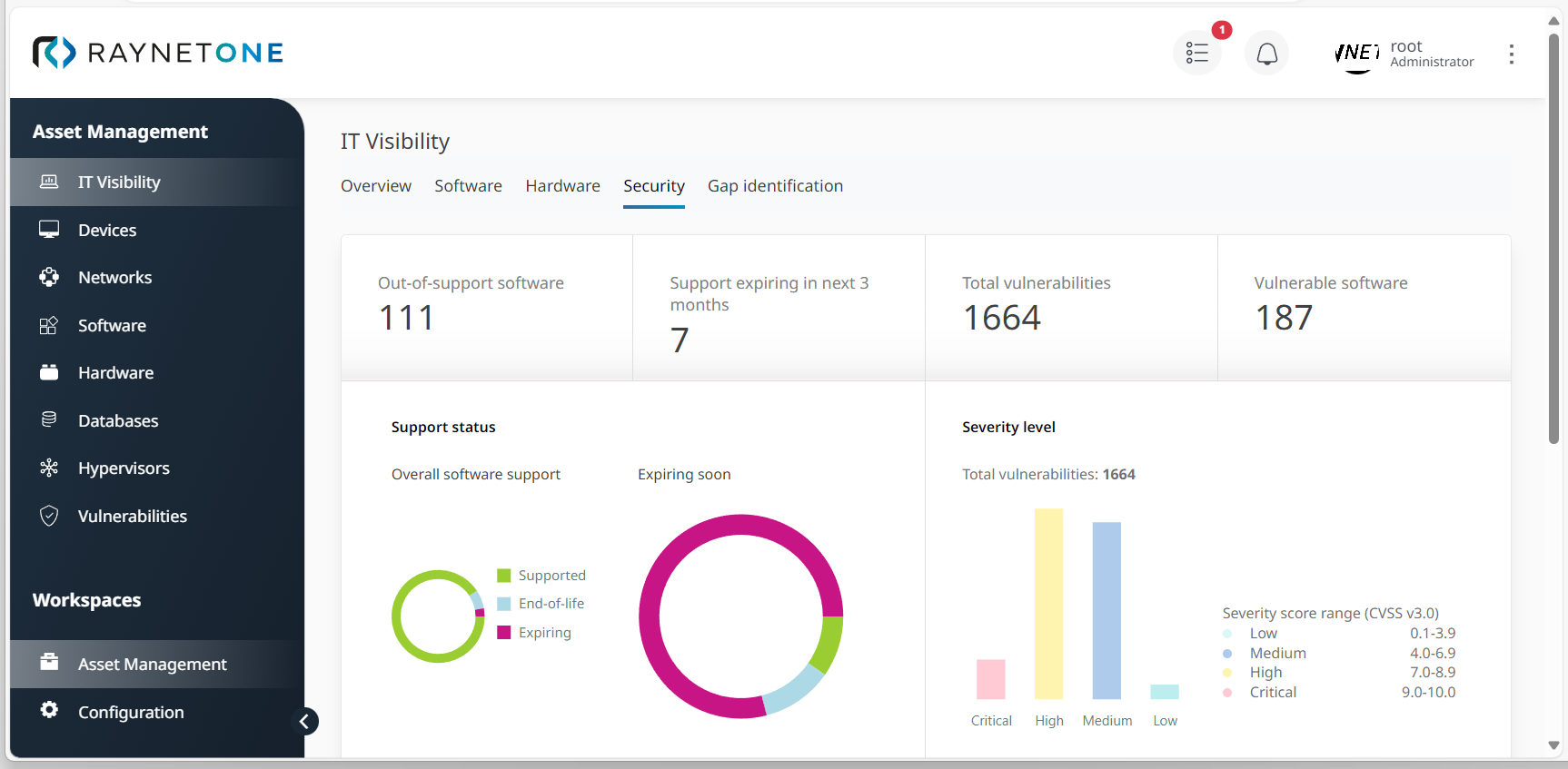
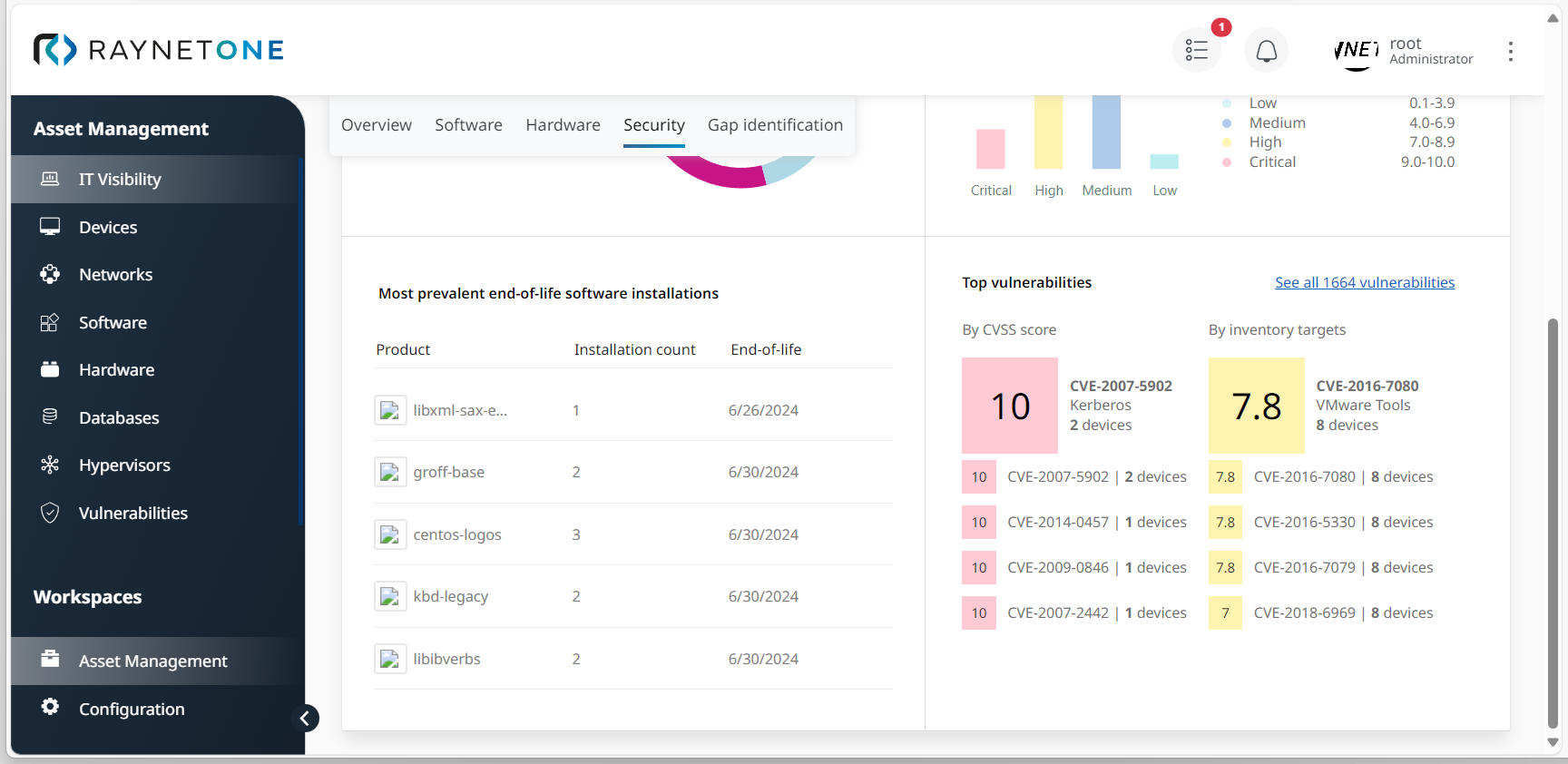
5.Open the Security tab to get a compact but accurate summary of your assets' support, vulnerability, and security status. Depending on your requirements, check the percentage of EoL and EoS software (under Support status), the Severity level of detected vulnerabilities, a list of Most prevalent end-of-life software installations, and the current Top vulnerabilities in different categories. Furthermore, you can open a list of all vulnerabilities to dive deeper into their details.
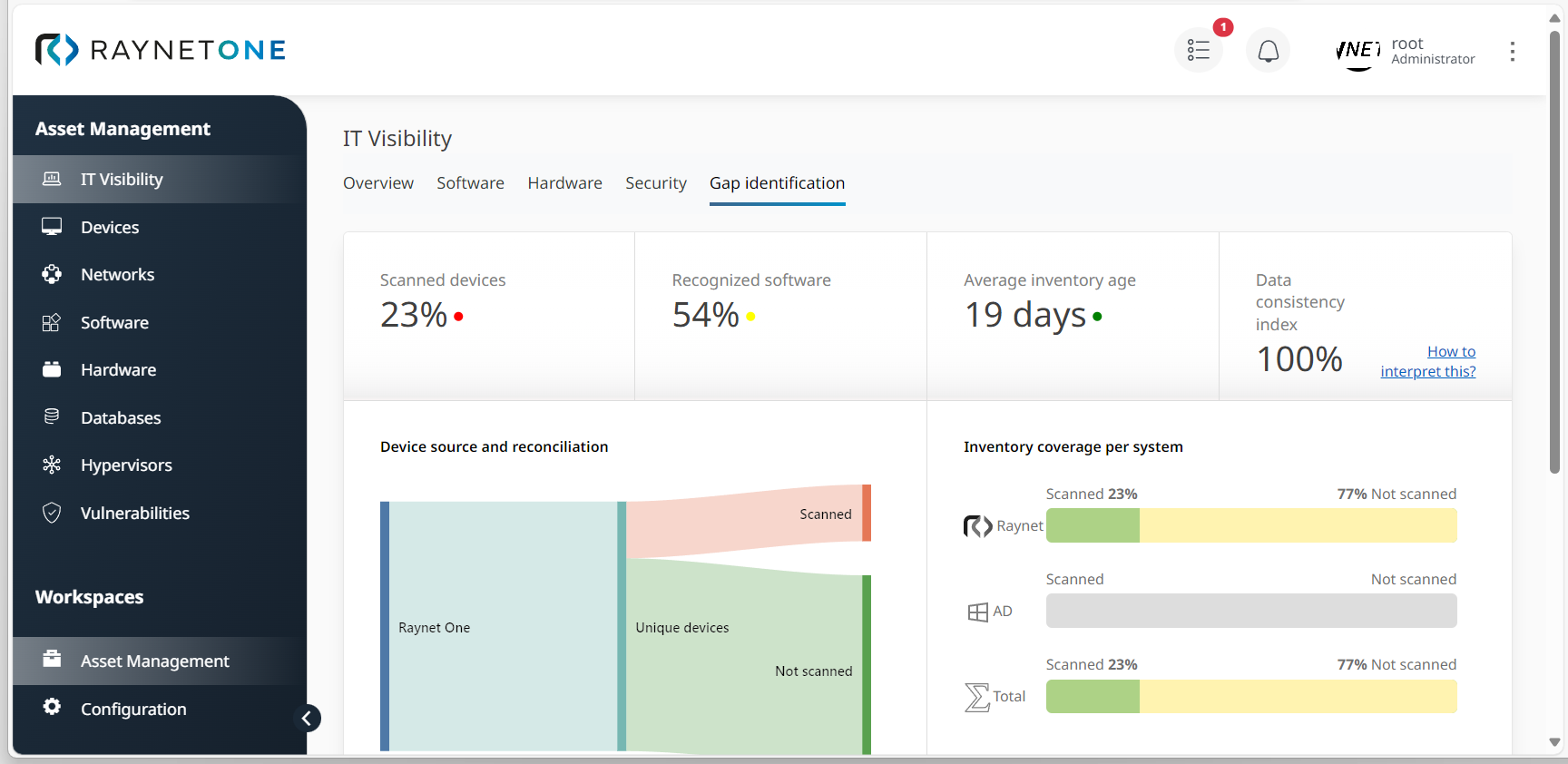
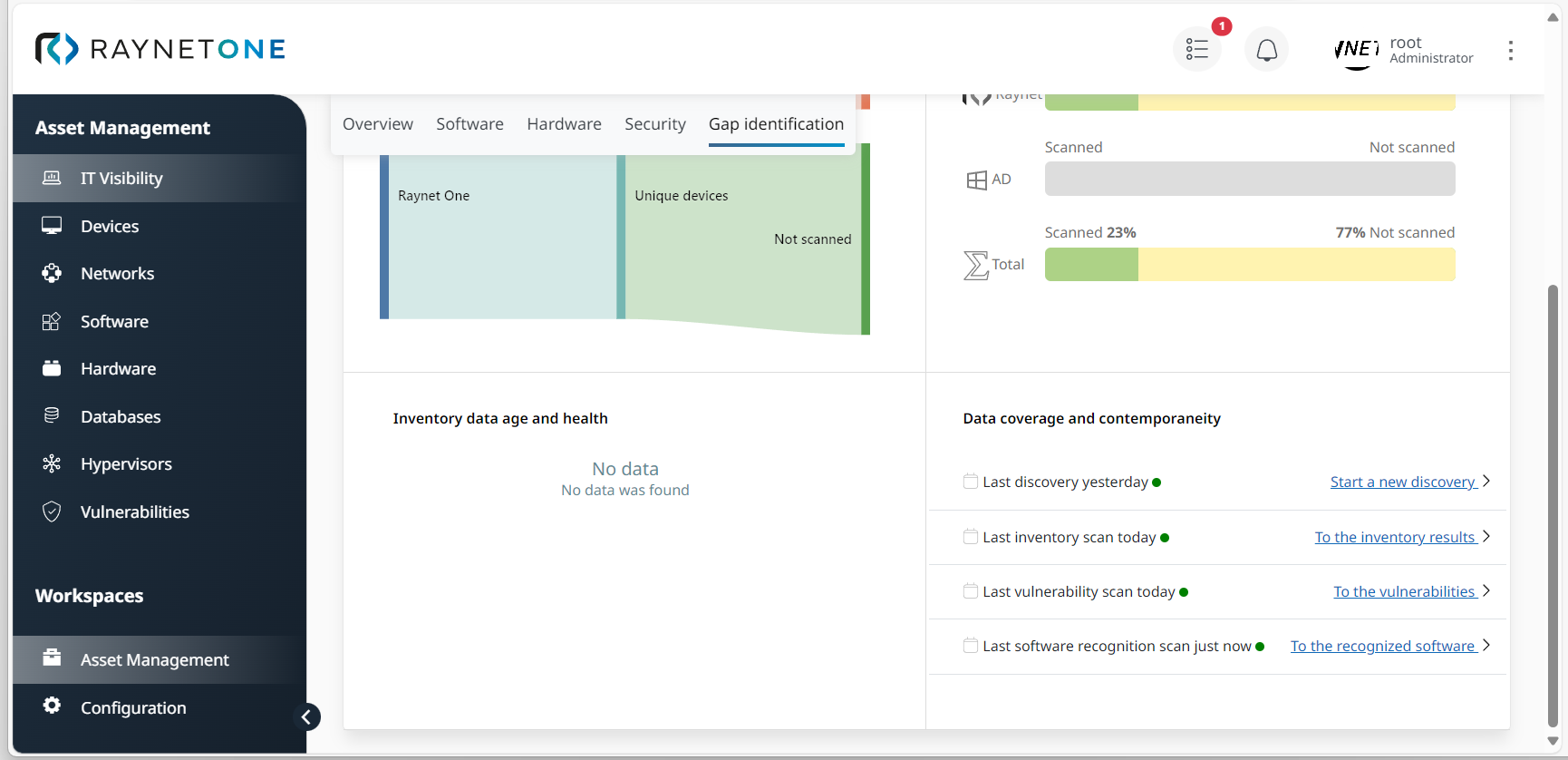
6.Under Gap identification, monitor the following sectors: Device source and reconciliation (relevant for inventory coverage rate). Inventory coverage per system (percentage of adequately scanned, discovered and inventoried assets), Inventory data age and health, and Data coverage and contemporaneity (overview on latest platform operations). Identifying inventory and discovery gaps in time is an important factor in monitoring your IT landscape's security as non-inventoried and non-scanned assets can always hold back security threats. Thus, they are potential sources of vulnerability.