A functioning IT landscape scan also relies on correct and precise discovery processes. As described in the Inventory Settings chapter, it might be useful or even required to adapt the platform configuration. The settings on this page are part of the resource scanning process. Their focus is on detecting new IT landscape resources. Decide on the set of enabled discovery instruments to control the detection approach. Specifically, choose between various technical methods to fine-tune the scanner's reliability. There are various options to specify how the system should respond to discovery results.
The Discovery Settings view includes two main tabs: Settings and Oracle.
In this view, you can perform the following actions:
•determining the inventory behavior when new devices are discovered,
•determining the inventory behavior when new Oracle databases are discovered, and
•viewing or changing the detailed configuration of Oracle instrument settings, port probing and SSH ports.
Settings
The settings on this tab are used to specify the system's response to the discovery result. In the event of newly detected network resources, you are provided with multiple behavioral options. Choose the right options to tailor the platform operation to your very needs and comfort. The options vary in automation and the need for user interaction.
More user interaction in the platform's proceedings leads to greater transparency. Use the optional user interaction hooks to assess the discovery processes inside of your IT landscape.
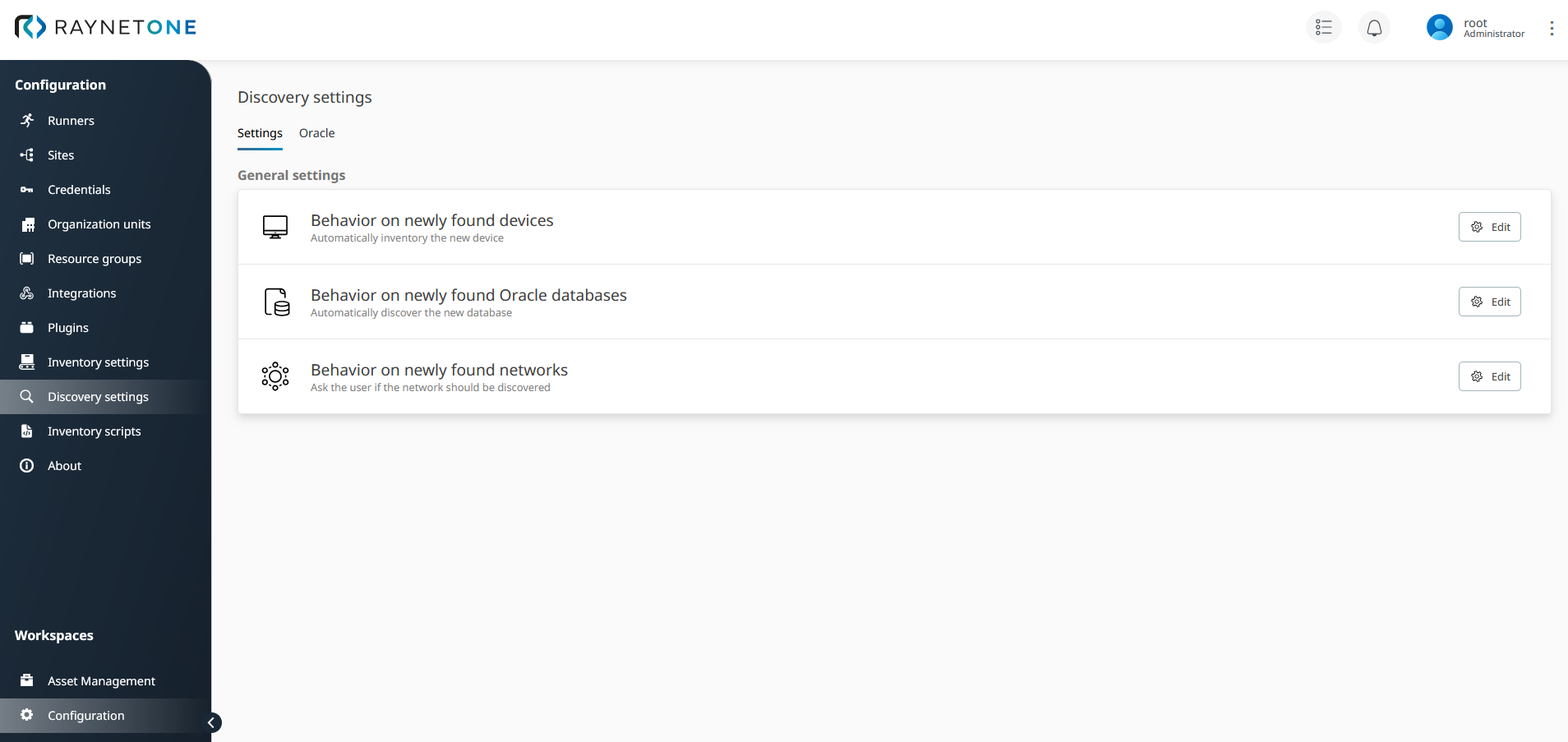
Settings tab of the Discovery settings view. Manipulate the displayed options to decide how the platform should deal with newly detected network resources.
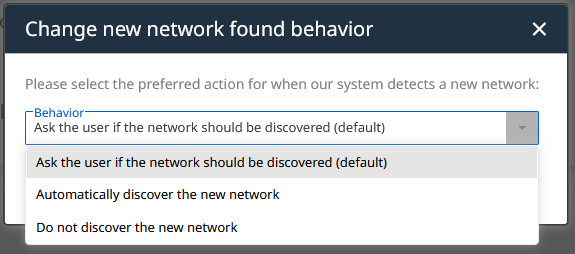
Example of changing the platform's behavior on newly found networks. As displayed in the image above, the combo-box of this widget offers you three configuration options. The default option is to ask the user in the event of newly discovered networks. This option enables user interaction in the discovery process. By choosing the second option, discovery is tailored towards automation instead.
Oracle
The Oracle discovery settings specify how the device scanner should find Oracle databases. Some options allow you to select the behavior in common discovery events.
The Behavior on missing credentials option allows you to enable user interaction in the critical Oracle database authentication event. If the credentials are missing, they are not found inside of the system database and there are no other means to query for credentials. Thus, only viable standalone option for the system is to fail the authentication and discovery. You can hook the missing credentials event to increase the leeway, the means of feedback by the IT landscape administration. The user interaction approach could be a viable option in controlled environments with a limited set of tightly managed devices, where a few credentials could pop-up, soon to be detected and registered.
The Port probing option defines the strategy in very early stages of Oracle device discovery. In TCP/IP networking, the application networking layer defines ports as means to address multiple applications on a device. Certain port types can be queried for connection willingness (also called "port probing"). Port numbers are commonly associated with known applications. Judging by the set of ports a device is listening for connections on, the Oracle database software availability can be assumed. Enable this option to collect and include port evidence into the Oracle database detection.
The Trigger inventory after discovery setting specifies on which condition the Oracle database inventory is triggered after discovery. You can choose to never follow-up with an inventory, to require the successful discovery beforehand or to always follow-up with an inventory.
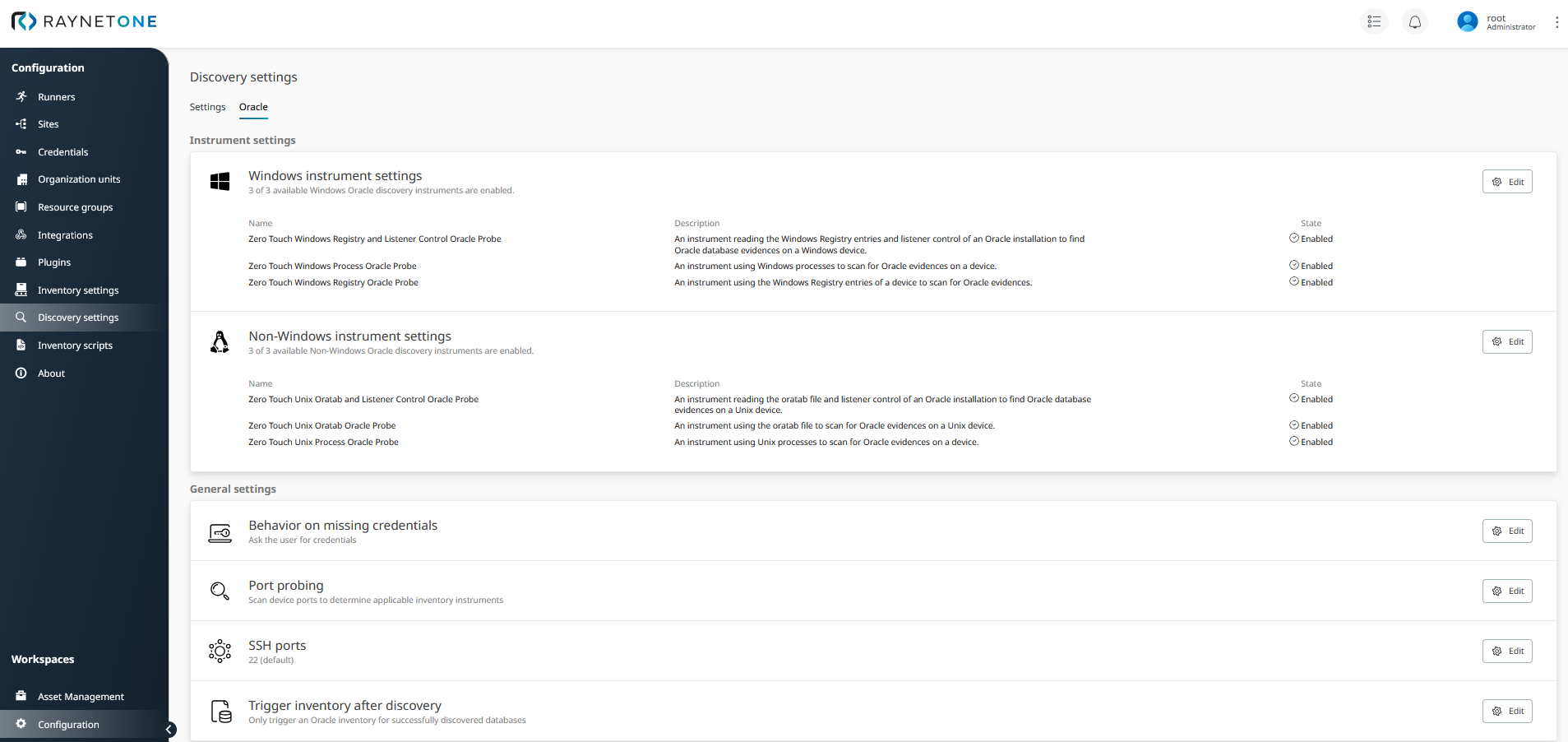
Oracle tab of the Discovery settings view. Many technical approaches are available to be configured in terms of Oracle database technology, empowering you to target many different IT landscapes.