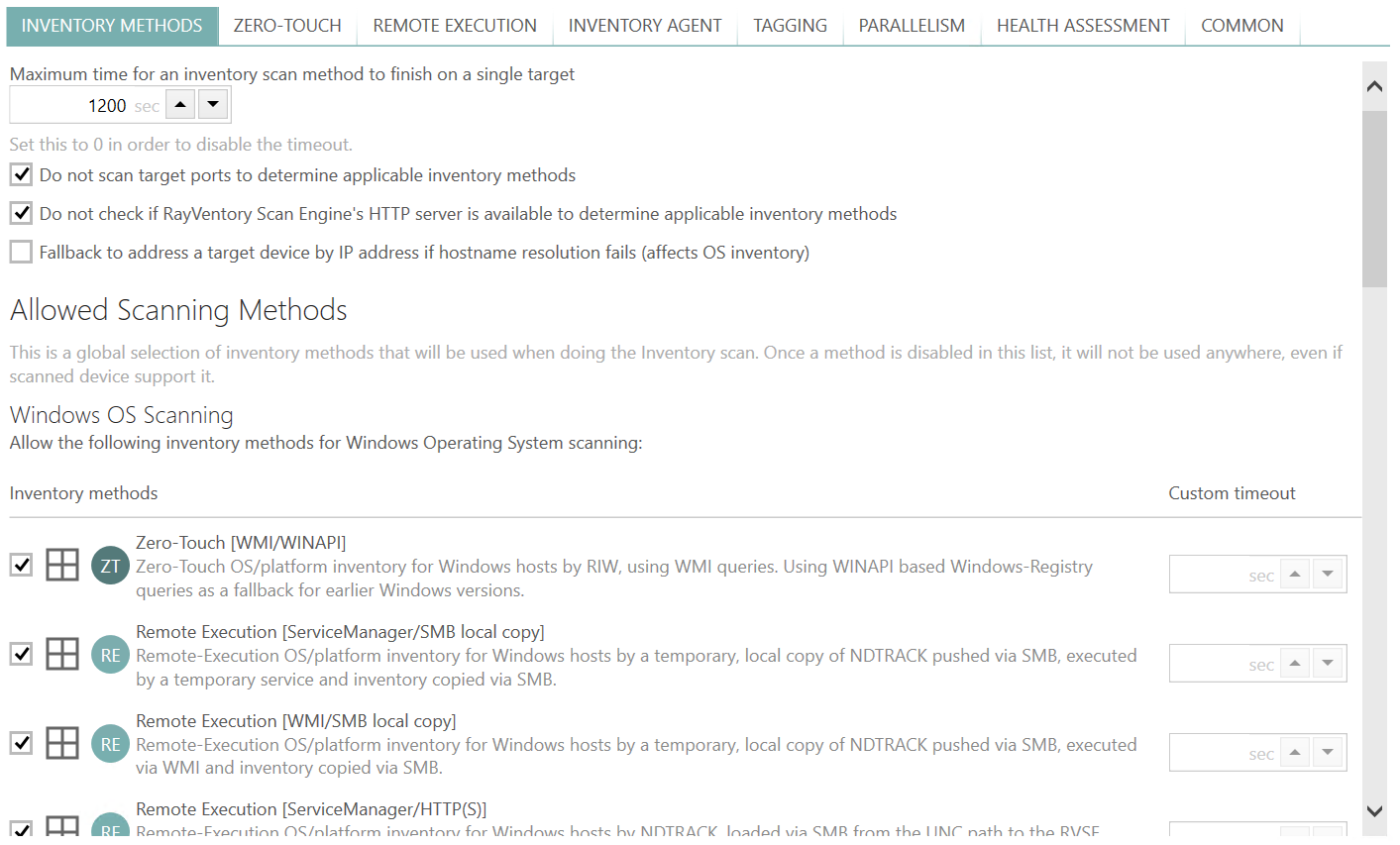
This tab is used to configure which inventory methods are globally enabled or disabled.
RayVentory Scan Engine supports up to 20 different methods which differ in:
•... where the work is being done (zero-touch from remote machine, or remote execution on the actual target machine).
•... the type of the Operating System (different set of techniques for Windows and Unix).
•... the way results are received back (via HTTP, file share, file access etc.).
•... the way in which remote execution is triggered (portable executable from share, a service, file access etc.).
The description next to each icon contains information about the target device family (in form of icon and textual description, either Windows or Unix), its name, and main characteristics of how it is actually working and where potential security pitfalls may lie. Within every group, the methods are sorted from what is agreed to be the "safest" method to some more invasive methods.
As a general rule:
•The methods described as "Zero-Touch" have minimal or zero impact on the target system. They usually connect to the target device via publicly available APIs or services and extract the data they need. No RayVentory Scan Engine process are executed on the host system. Methods from this family are less "intrusive" than remote execution, but may sporadically be limited by functionality of underlying APIs, services, and exposed endpoints. As a rule of thumb, you should try to start with zero-touch methods and verify whether the incoming results are satisfactory and move to the remote-execution in the next step, should some devices or networks require them.
•Methods described as "Remote Execution" may potentially have impact on the target system to some varying degree. Depending on the method type, some of them may try to install a service and almost all of them execute scan utilities bundled with RayVentory Scan Engine. After each execution a necessary clean-up is done (for example removing the temporary service and / or files), but the machine may be impacted in one or more ways just because of some processes being physically started on it. While these methods are considered more "intrusive", they tend to deliver better results as they have better access to the necessary resources and databases.
|
Note: You can read more about differences between the different methods in the following chapter: Inventory Methods Overview. You may review them with your system network administrator to find out which methods should be allowed or disallowed in your environment. |
Enabling or disabling any method is done by a mouse click:
•Tick a checkbox next to the name of the method to enable it.
•Untick it to disable it.
The icon and badge are dimmed if the given method is disabled.
Once the method is disabled here, it will no longer be considered by any inventory scan, even if the target device supports it. For example, if you disable remote execution on Windows and Unix from this screen, only zero-touch methods will be considered for your devices.
Timeout per method
It is possible to define a timeout, which - regardless of global settings - will be then used for a particular family of methods. To define it, enter the required value into the Custom timeout column. Leave the column empty to not use any method-specific timeout.