In order to call the Microsoft Graph API an access token from the Microsoft identity platform is needed. The access token contains information about the connector and the permissions it has for the resources and the APIs available through Microsoft Graph. The connector must be registered with the Microsoft identity platform and be authorized by either a user or an administrator for access to the Microsoft Graph resources needed.
Register the Connector With the Microsoft Identity Platform
Integrate the connector by registering it with the Microsoft Identity Platform and thereby establish the information that is used to get tokens:
•Application ID: A unique identifier assigned by the Microsoft Identity Platform.
•Redirect URI/URL: One or more endpoints at which the connector will receive responses from the Microsoft Identity Platform.
•Application Secret: A password or a public/private key pair that the connector uses to authenticate with the Microsoft Identity Platform.
In order to access the Azure Compute APIs, for each Azure Tenant that should be connected to Data Hub, an App needs to be registered that acts as a service principal (i.e. technical user).
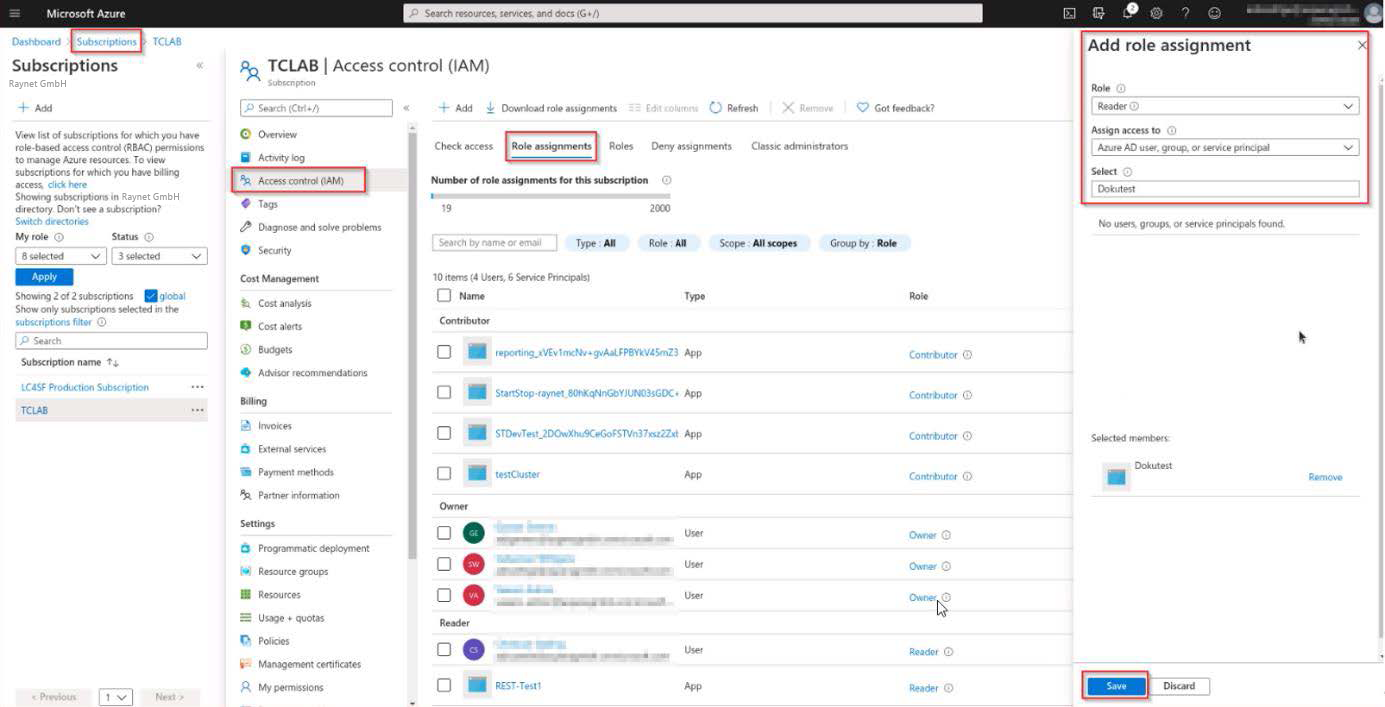
The App should have "Reader" rights assigned for all subscriptions in the scope.
For each Azure Tenant that should be connected to Data Hub perform the following steps in the Azure portal:
|
Note: As an alternative to manual configuration in the portal it might be necessary to use the following Azure CLI command to perform the task:
az ad sp create-for-rbac -m "USUApp" --role Reader
On success, the required app credentials will be returned to the standard output in JSON format. Make sure to properly copy and save them!
The following link provides more detailed information, e.g. it explains how to scope the role-based access of a Service Prinzipal to select subscriptions: https://docs.microsoft.com/en-us/cli/azure/ad/sp?view=azure-cli-latest#az_ad_sp_create_for_rbac. |
1.Register an Application (name and URL do not matter; the application type has to be "Web-App/API"):
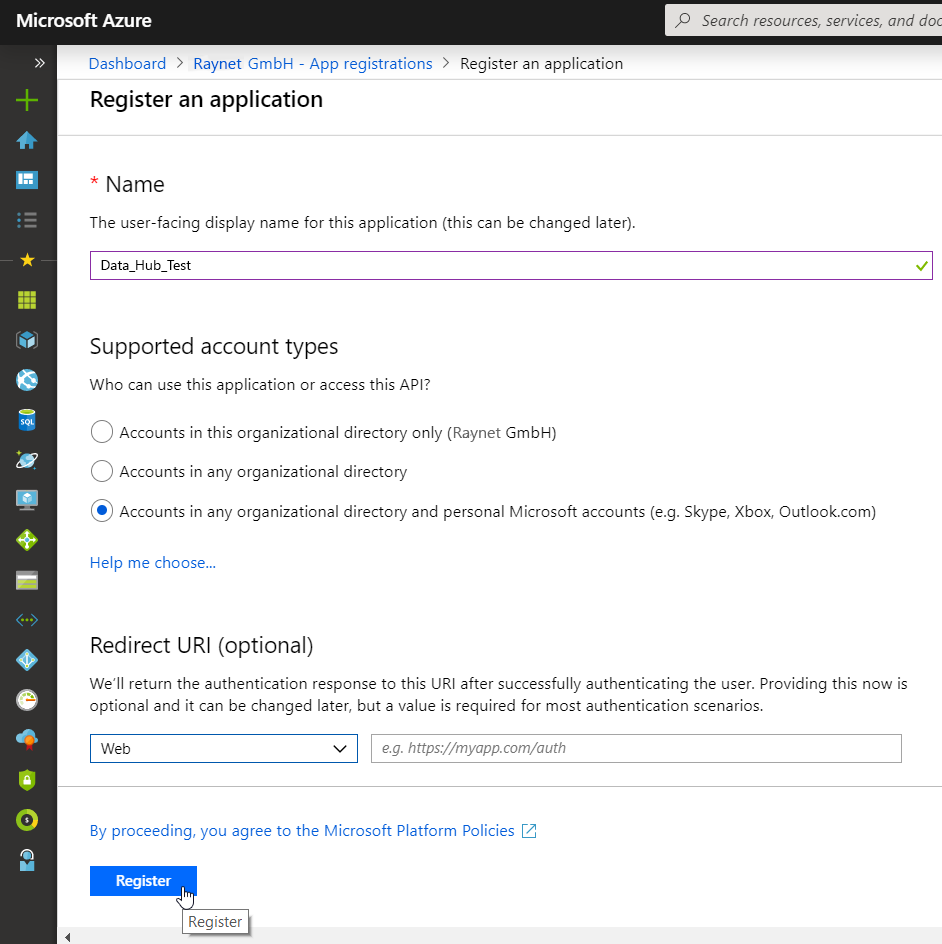
Supported account types |
Description |
|---|---|
Accounts in this organizational directory only |
This option maps to Azure AD only single-tenant.
This is the default option unless the app is being registered outside of a directory. In cases where the app is registered outside of a directory, the default is Azure AD multi-tenant and personal Microsoft accounts. |
Accounts in any organizational directory |
This option maps to an Azure AD only multi-tenant.
If the connector has been registered as Azure AD only single-tenant, it can be updated to be Azure AD multi-tenant and back to single-tenant through the Authentication blade. |
Accounts in any organizational directory and personal Microsoft accounts |
This option maps to the Azure AD multi-tenant and personal Microsoft accounts.
If the connector has been registered as Azure AD multi-tenant and personal Microsoft accounts, it cannot be changed in the UI. Instead it is necessary to use the application manifest editor to change the supported account types. |
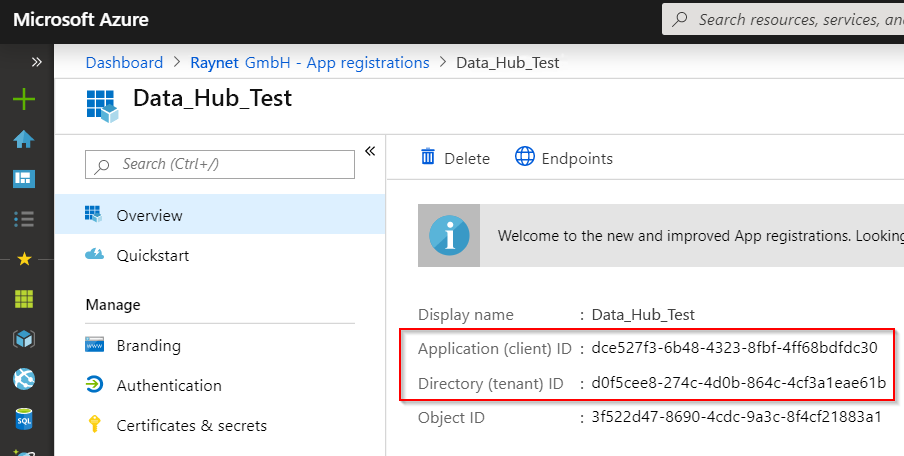
2.Lookup the Application ID and the Directory ID and note them down:
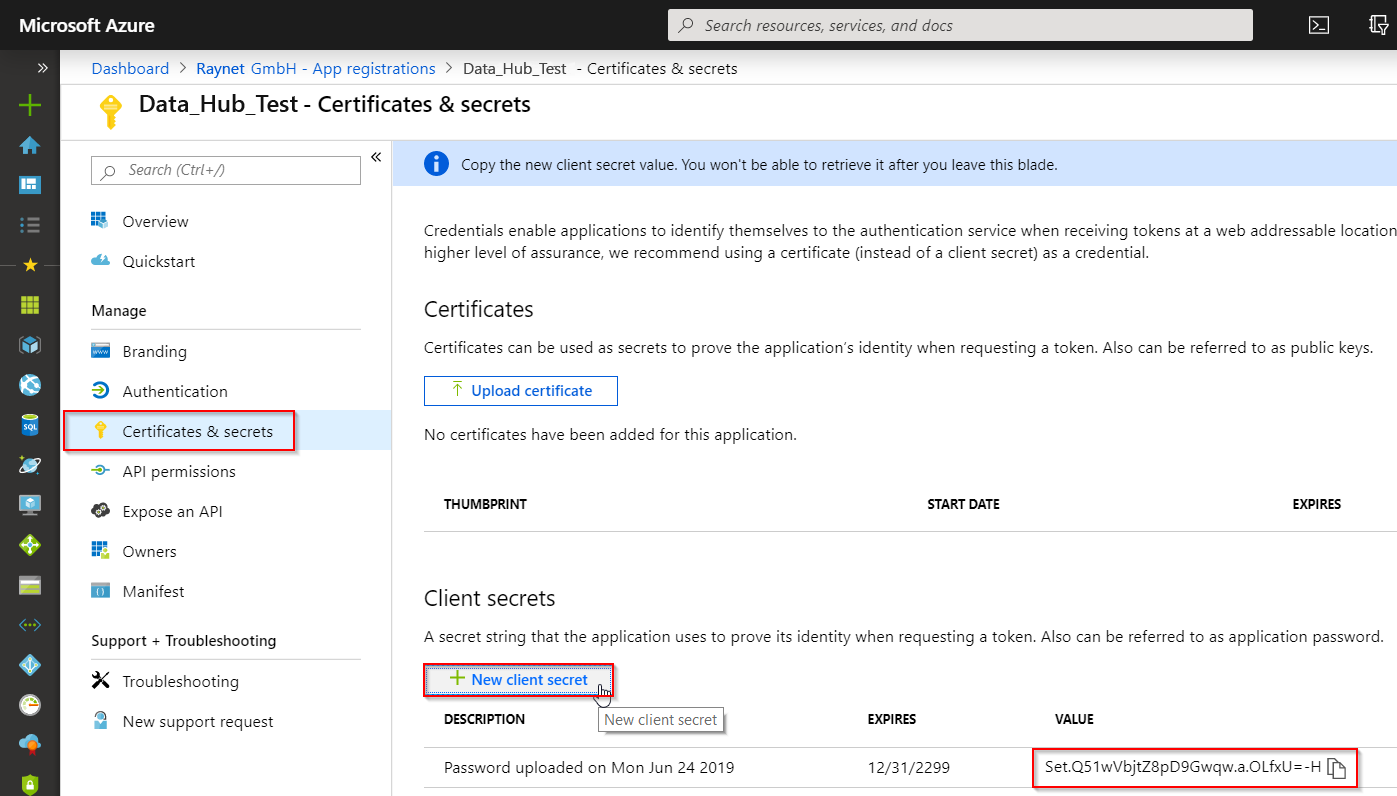
3.Create a secret (Key) and not it down:
4.Assign the "Reader" role to the application:
Additionally, access to the LogAnalytics Workspace where the data from Azure Automation/Inventory is stored is also required for this connector.