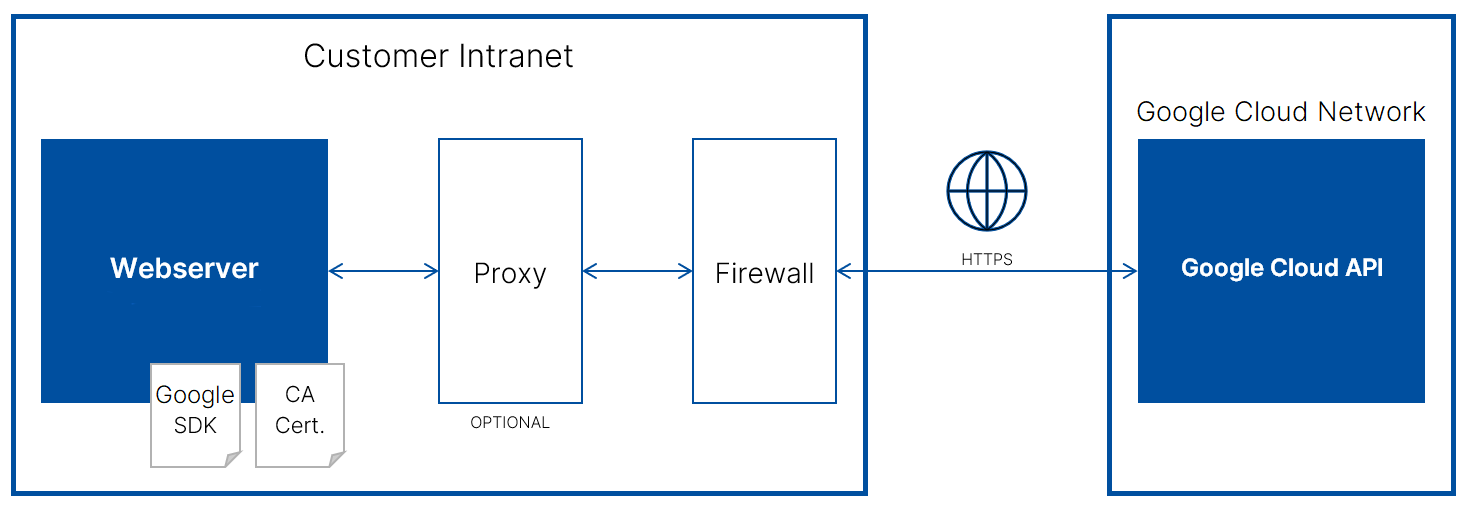
In order to use the connector, it is necessary to create a Service Account Key JSON as explained in the official documentation https://cloud.google.com/docs/authentication/production#create_service_account. Download it to the local machine and extract the necessary data from the JSON file for the operation of the connector.
Authentication and Authorization
To use one Service Account Key in multiple projects it has to be added in IAM of other projects. The connector requires the following scope for authentication: https://www.googleapis.com/auth/cloud-platform.
For authentication to the REST APIs, for each Google account a private key (JSON file) has to be created in the Google portal and stored on the server. The required configuration is described below.
For each Google Cloud Account that needs to be connected with License Manangement, perform the following steps in the Google Cloud portal:
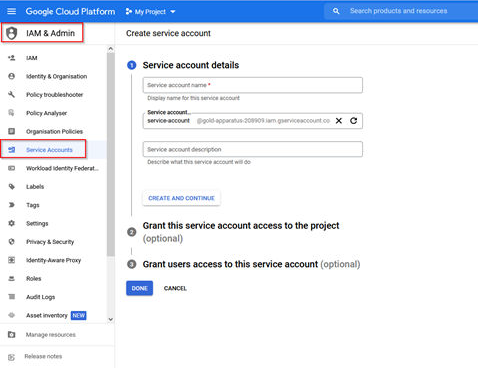
1.Select the project where the Service Account should be created (it will then be possible to give the appropriate permissions to the other projects with the same service account).
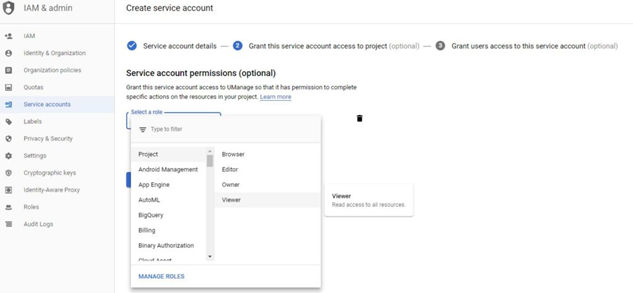
2.Create a service account. After creating the account, grant it the viewer role, then authorize a virtual instance to run as that service account.
3.For a service account, download a private key and store the .json file that is to be used to run the connector.
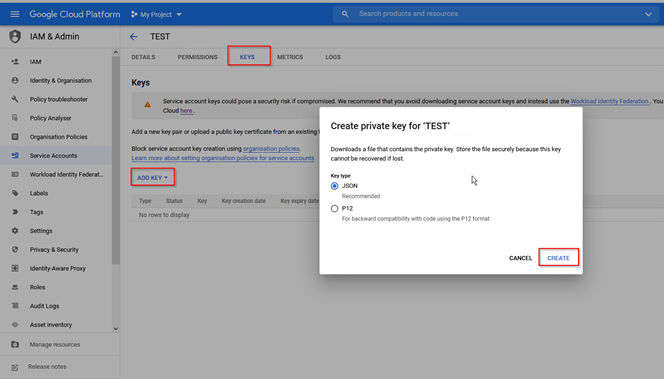
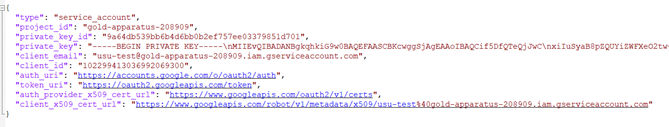
4.Save the file locally.
5.Activate the appropriate / required APIs
In order to use one Service Account Key in multiple projects, it has to be added to the IAM to other projects.
1.Create a service account within the Service Accounts section.

2.Add to the IAM section of the cross project.
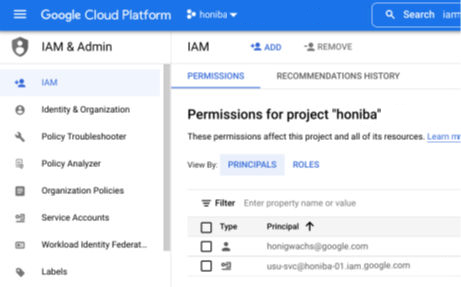
Generally, the organization, folder, and project structure should already be present whether a project is exempt or should be included in the inventory management.
These are than managed by policies. This is the best way of organizing access for the service account.