Connections between machines in any size of network go through multiple machines. The transferred data is open for any of the participating machines to see, but the actual meaning is hidden behind means of encryption. The cryptographical keys are kept hidden as secrets, just exposing the public key or certificate for decryption and signature verification purposes.
The public certificate contains the public key. It is distributed to all connection partners that trust your server. Incorrect management of certificates will lead to SSL / TLS connection issues. This is why maintaining the Public Key Infrastructure is important. In this chapter we want to highlight key points about its maintenance.
Identifying the Windows certification authority root certificate
Each Windows domain holds a root certificate. It signs the certificates of all computers in the domain. Thus, network communications associated with the domain are trusted and secure.
To identify the domain root certificate, you should log in as network administrator to the Windows server machine with the Certification Authority role installed. Then, open the Certification Authority MMC snap-in.
Press the Windows key and type in certification authority to quickly open the MMC snap-in on English locale.
You should see a window with the text certsrv in the title.
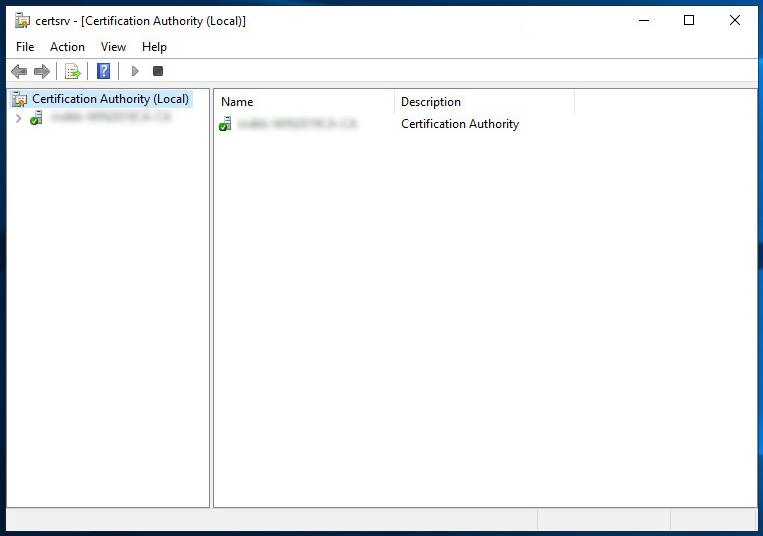
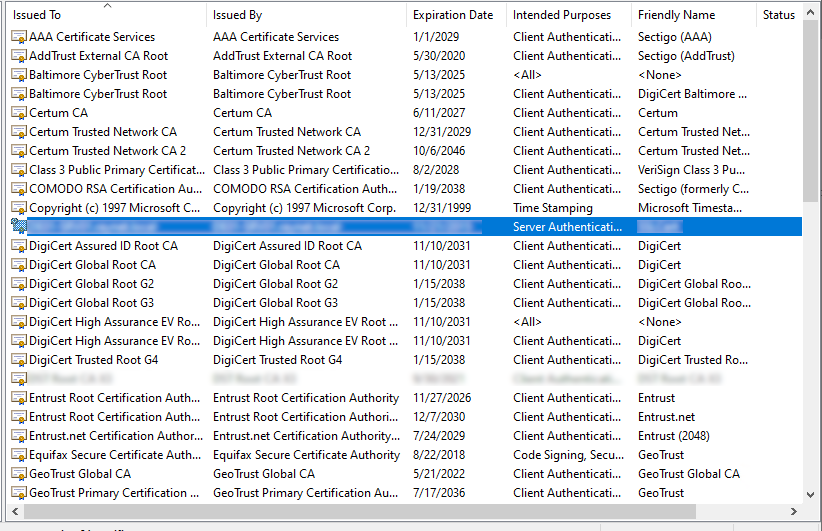
In the list on the right side you see all of your certification authorities associated with your Windows domain. Usually, there is only one CA listed. Right click on the CA and select the Properties option.
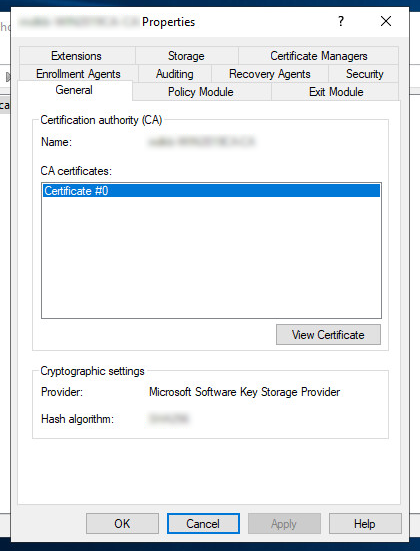
The certification authority manages a list of certificates. These CA certificates are the root certificates in our Windows domain PKI.
Click on the View certificate button to open the root certificate. You will be presented with a new window with certificate details. The name of your root certificate is written after the Issued to: text.
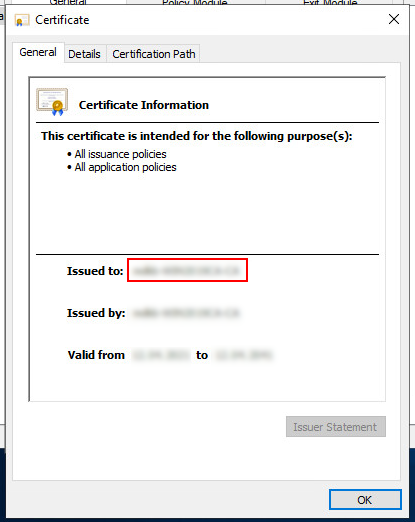
The details view of our Windows domain root certificate. Since there is no certificate above that signed it, the details show the same text for Issued to and Issued by.
Installing root certificates on Windows computers
Root certificates have to be installed manually on several occasions. One example is the Windows computer outside of the Windows domain. Here is a simple method of certificate installation on a single computer (for example the Raynet One runner).
First, open the MMC snap-in responsible for local computer certificate management. On English locale, you can press the Windows button and type in Manage computer certificates.
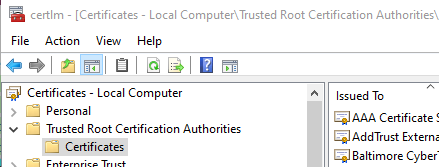
The Windows computer certificate storage management snap-in of MMC. Use it to verify and install trusted signing root certificates.
You see a window with the text certlm in its title. On the left you see a tree-view of different certificate categories. Identify the category for trusting root certification authorities and expand it. Then, click on its Certificates node. The list on the right should now display all trusted root certificates respected on your local computer.
Right click on the Certificates node and click on All tasks > Import. The Certificate Import Wizard opens up.
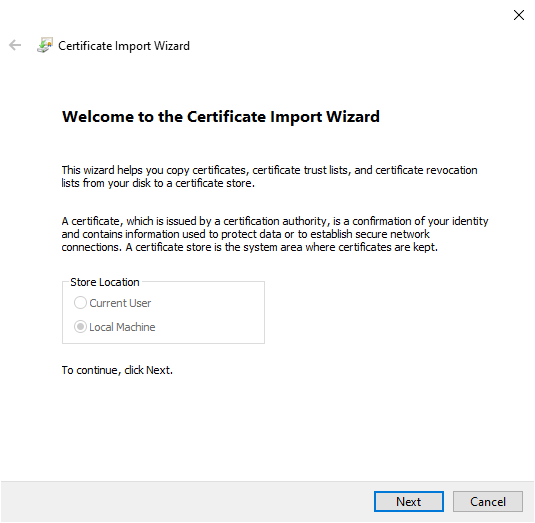
Click on Next. Select the certificate file that you want to import in the subsequent prompt. Finish the wizard to complete addition into the trusted list.
Finally, verify the certificate import by looking at the list in certlm.