This chapter explains an alternative method of Windows credentials assignment to Windows runners. It leads to less credentials distribution/spread across varying technology, if compared to credentials addition in the web interface. Empower automated coordinated runner deployment related to the smart choice of Windows credentials and Windows deployment scripts. It enables robust runner integration into established Windows Service management strategies which may incorporate dynamic credentials (re-)assignment.
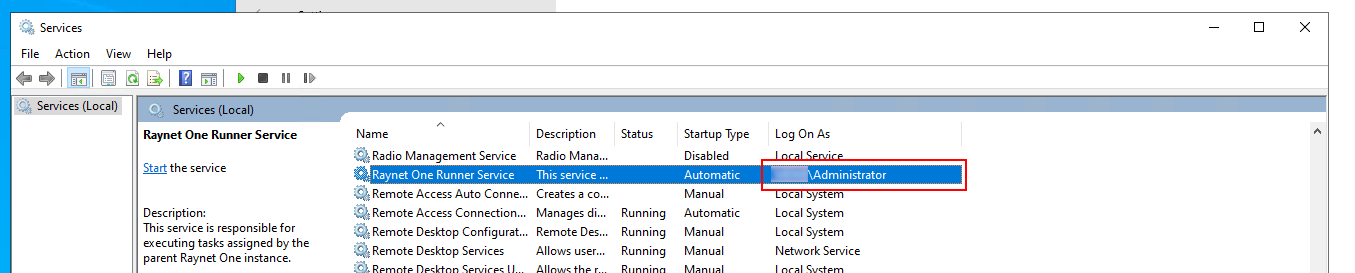
The Windows Service management application displaying the Raynet One Runner Service entry. The Log On As column cell value is the Windows user to execute the runner application. By issuing jobs to the runner and requesting the use of current Windows session credentials, the assigned Windows service user is used for Windows network resource authentication (Windows devices, AD or MECM).
Installation steps
You have the option to specify Windows user credentials during runner installation. The input form is presented on the Service user identity page. Simply click on the radio button labeled Custom account to enable the input boxes. Prior to runner installation, make sure that the selected Windows user has got the Log On As A Service right explicitly assigned to him. The rights assignment to the Everyone Windows user group may not suffice.
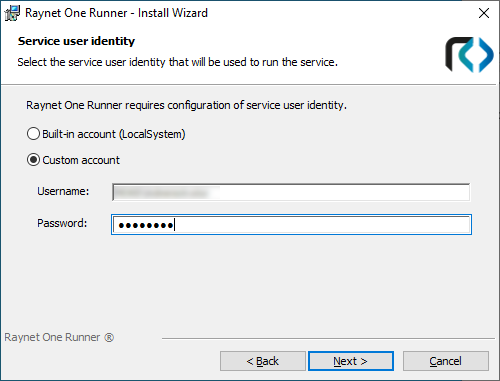
The Service user identity page of the runner installer providing the input form for Windows service user credentials.
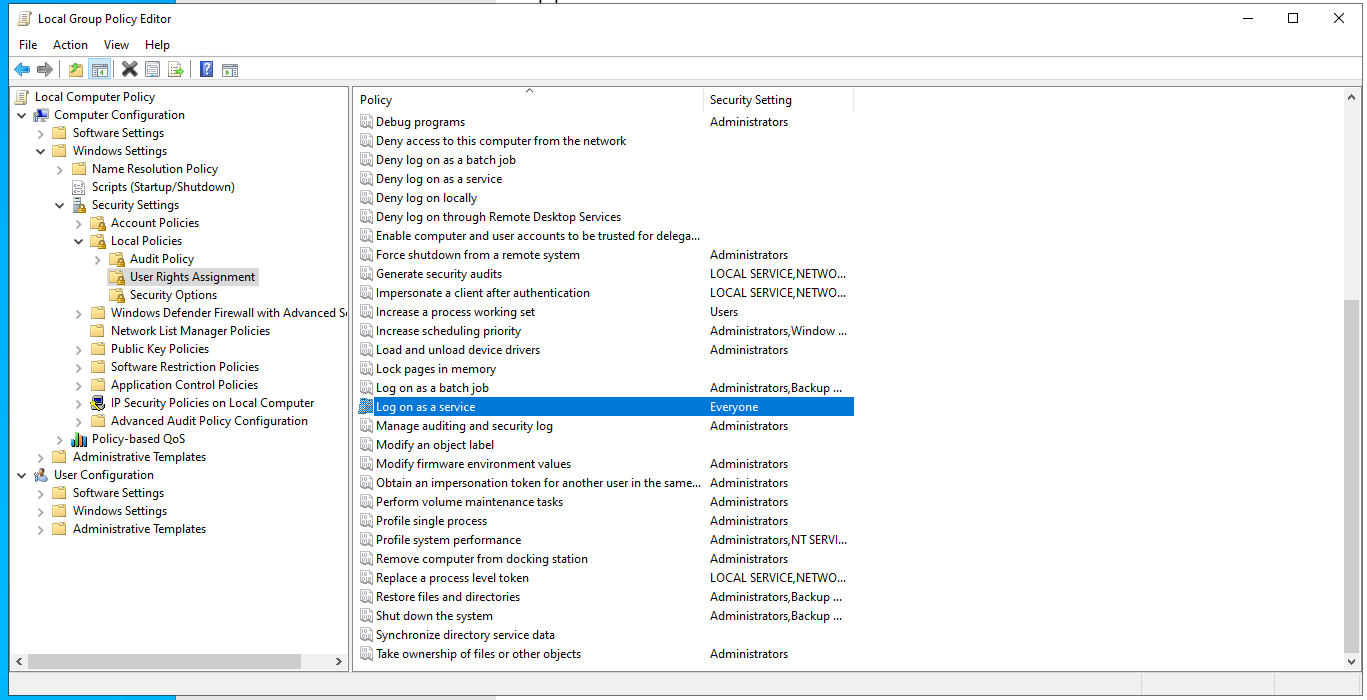
The Windows Group Policy editor showing the location of the Log on as a service group policy setting. As displayed by the Everyone Windows user group, only local machine users are allowed to log on as a Windows Service. Explicitly assign Windows domain administrators to allow the runner to operate using strong credentials. Before starting the runner this way, properly secure the runner executable files and their resources against tampering by lower privileged users.