Leverage the power over your IT landscape devices by requesting command execution across all of the registered devices. Validate the connectivity to important network resources. Perform maintenance tasks using specially crafted device scripts. Prepare devices for maintenance by putting them into a special state. Collect device command inventory for monitoring purposes.
In this use-case, we use the ping command for example.
Supported OS types: Linux, Windows
Program content (inventory script)
def main():
content = None
osf = PythonConnector.os_family()
if osf == "Linux":
lines = PythonConnector.run("ping -c 3 microsoft.com | base64")
content = "".join(lines)
elif osf == "Windows":
lines = PythonConnector.run("ping microsoft.com")
content = "\n".join(lines)
else:
PythonConnector.info("unable to collect ping inventory for unsupported platform")
return
F = PythonConnector.create_item("File", "PingCollector Blob", False)
PythonConnector.add_property("Name", "//ping", F)
PythonConnector.add_property("Content", content, F)
PythonConnector.add_property("Manufacturer", "PingCollector", F)
PythonConnector.add_item(F)
PythonConnector.info("Collected ping inventory")
main()
API fetching program requirements
•Python 3+
•Requests library (https://docs.python-requests.org/en/latest/)
•RNO API key
•RNO frontend URL
API fetching program (displayinv.py)
import requests
import base64
APIKEY = "PUT API KEY HERE"
FRONTEND = "PUT FRONTEND URL HERE"
HEADERS = { "ApiKey": APIKEY }
def obtain_paged(EP):
P = {}
P["count"] = 1000
items = []
while True:
result = requests.get(EP, params=P, headers=HEADERS)
if result.ok == False:
break
objs = result.json()
if objs == None:
return
if len(objs) == 0:
return
items.extend(objs)
lastobj = objs[len(objs)-1]
P["LastId"] = lastobj["id"]
return items
def main():
files = obtain_paged(FRONTEND + "/api/v1/File")
if files == None:
print( "failed to obtain frontend files (" + FRONTEND + ")" )
return
print( "Ping results of devices" )
print( "=====================" )
any_ping_result = False
for F in files:
if "deviceId" in F and "name" in F and "content" in F and F["name"] == "//ping":
print("*** Ping result for device " + F["deviceId"] + ":" )
try:
DC = base64.b64decode(F["content"], validate=True)
print(DC.decode("latin-1"))
except:
DC = print(F["content"])
any_ping_result = True
if any_ping_result == False:
print( "none" )
Screenshots
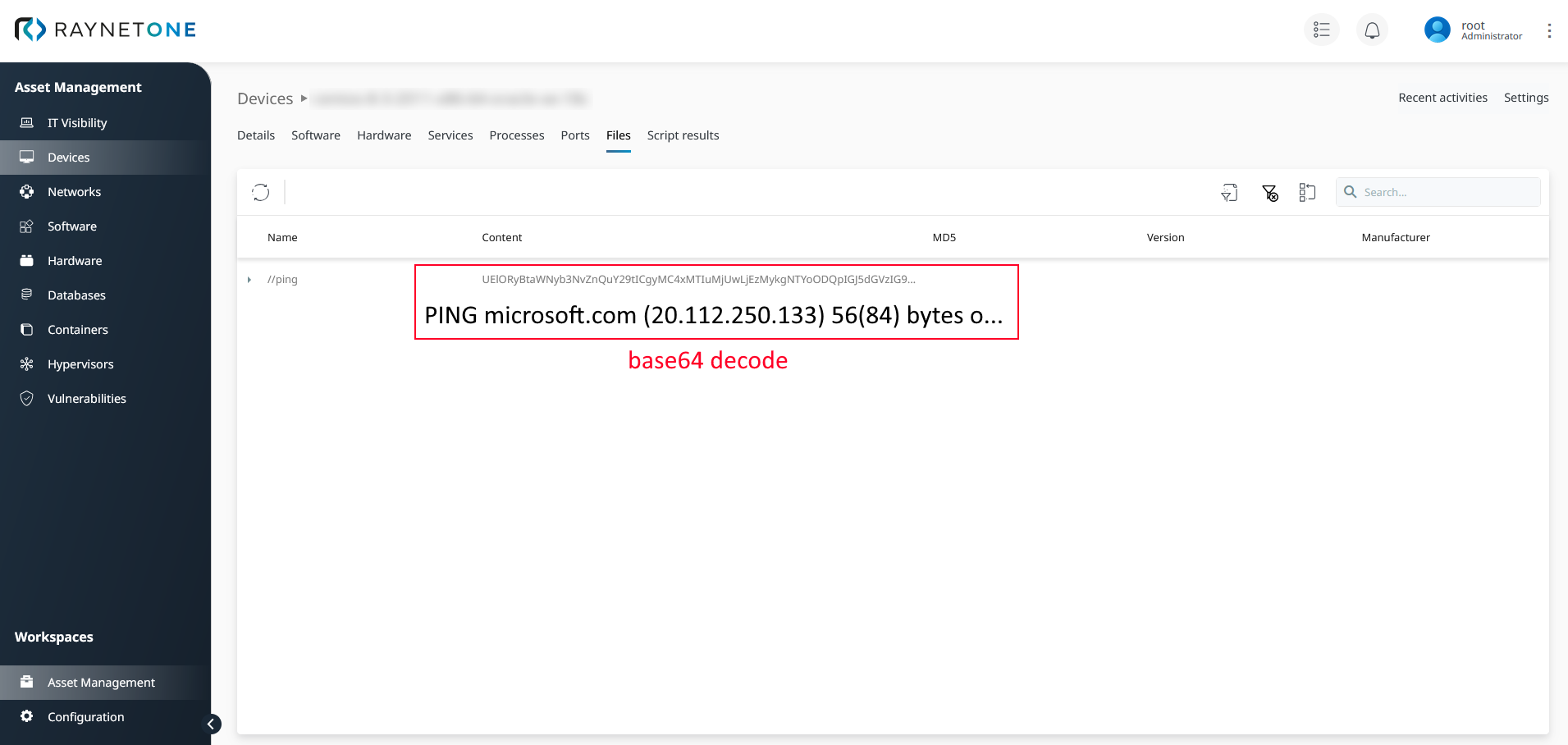
The ping results displayed in the web interface device details view. The inventory script results are visible on the Files tab. There is an entry called //ping. The content column contains a base64 representation of the ping command output. By decoding the base64 encoded string back into its raw form, you can see that the domain microsoft.com was pinged.
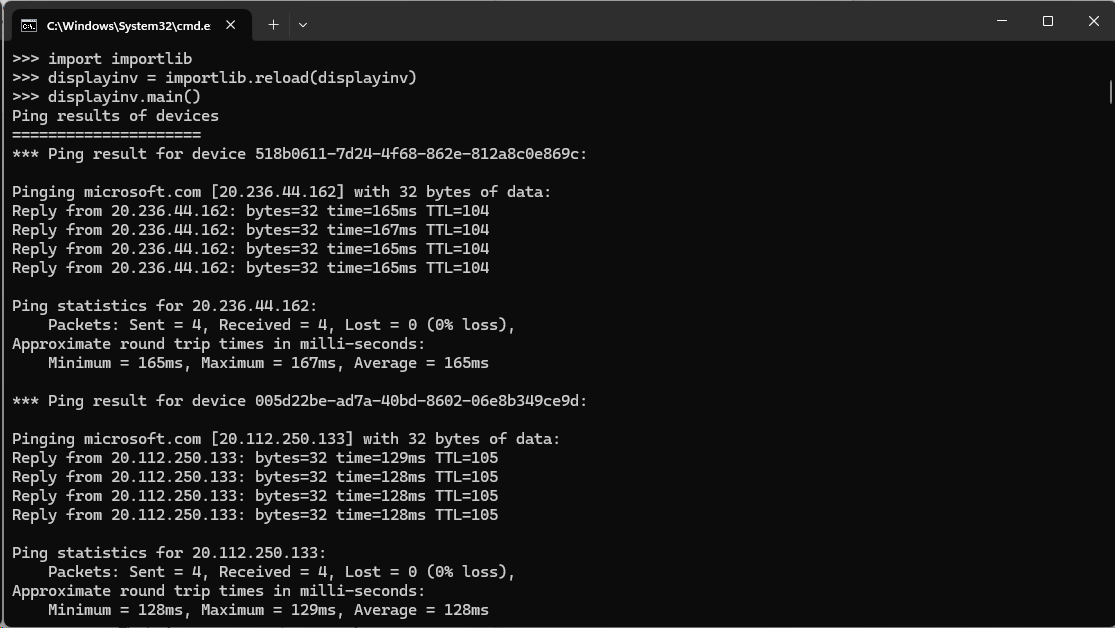
The executed API fetching program after collecting the ping inventory. It displays a list with the header "Ping results of devices". Then, a list of devices follows. Each device entry starts with the device id. After the device id, the ping command output follows.