Credentials are used to access IT landscape resources such as devices or Oracle databases. During device inventory operation, relational data to IT landscape resources is collected to better understand the meaning and application of the credentials. For example, the last-known-good credentials are remembered to retry another connection using them in the future. In this chapter, important details related to credentials selection behaviour are presented.
Linux device inventory evidence
On many Unix devices, Secure Shell (SSH) is used for connection and authentication. On the Debian Linux distribution, execute the $ sudo journalctl -t sshd shell command to view SSH log-ins to the device. This log can be used to verify the selection of credentials for device inventory.
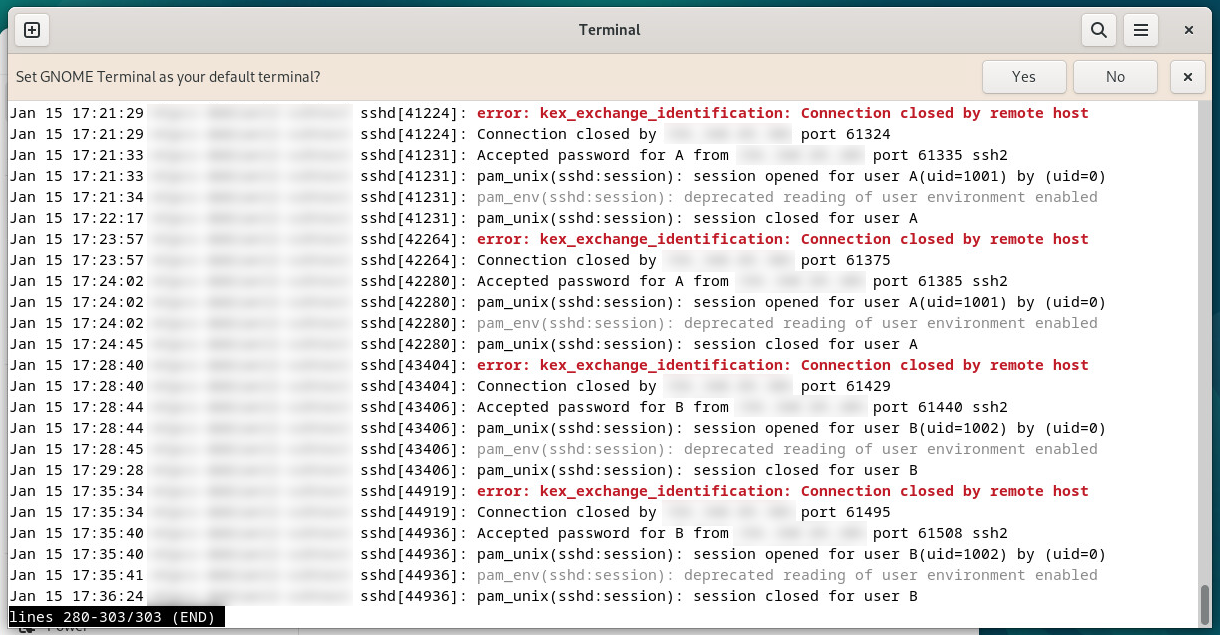
An example of device inventory log-in evidence collection per SSH onto a Debian 12.5 device. Other Linux distributions may come with similar authentication attempt protocols. In those logs, you can see both successful and failed log-in attempts.
The last-known-good credentials
If device inventory succeeds, the used credentials are remembered as last-known-good credentials. As long as this relationship exists, the next device inventory attempt of the device will first try authentication with the same credentials. This logic is meant to reduce the amount of credentials authentication attempts, optimizing the device inventory process.
New credentials with possibly greater permissions do not override last-known-good credentials automatically. The update can be forced by deleting the last-known-good credentials. Doing so will push back the device inventory process to pick from the set of all credentials.
Authentication failure removes the last-known-good relationship.
The Username column of devices is a hint of the last-known-good credentials. It does not show the last-known-good credentials if the credentials were deleted.
Removing certain credentials assignments (to devices or sites) does invalidate last-known-good relations. An exception to this rule is the change in regular expression.
Prompting the web interface user for credentials
After exhaustion of all applicable credentials to the network resource, the web interface user is prompted to fill in the credentials by default. For the duration of this prompt the device inventory process is waiting. Any other device inventory processes continue as usual in parallel.
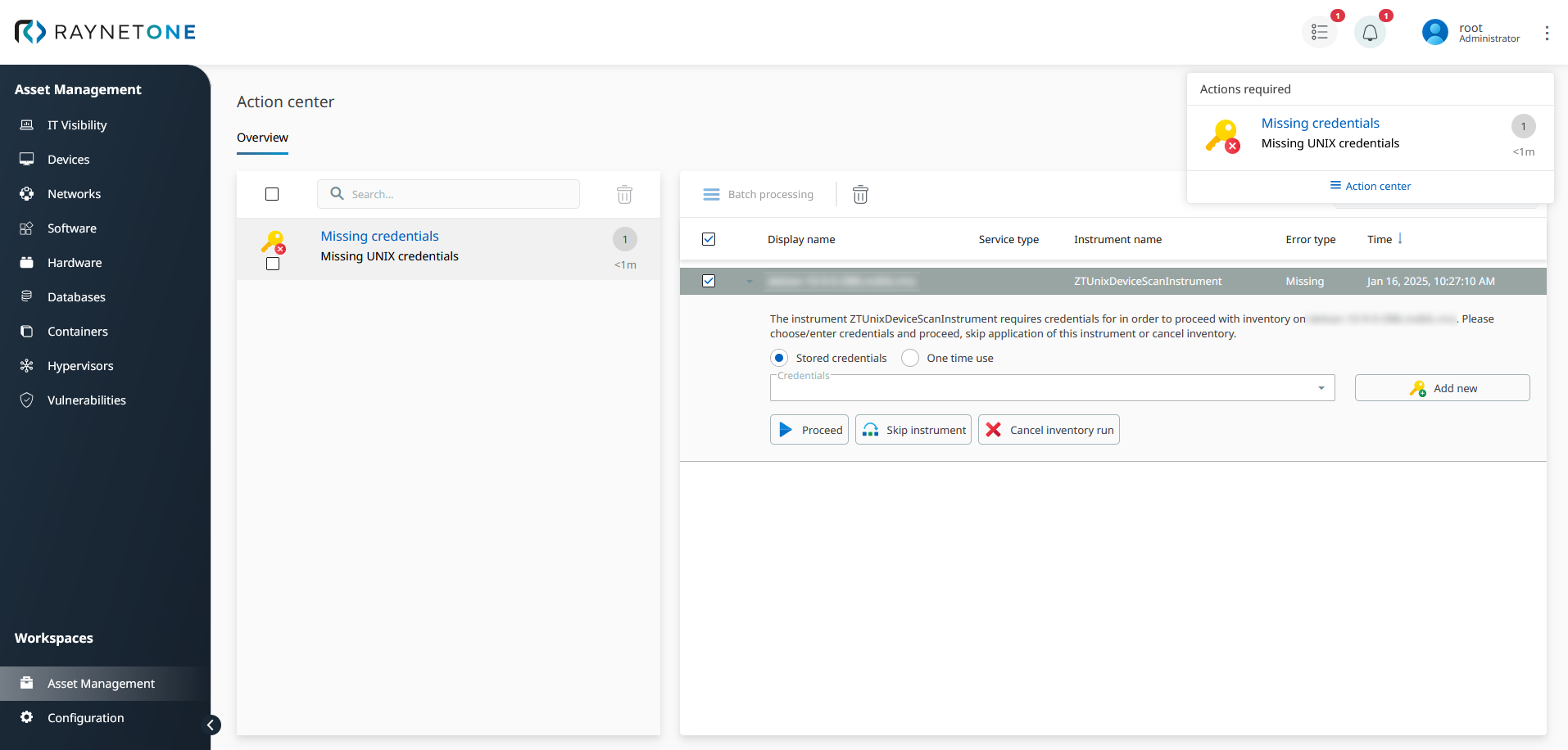
The provided user interface for completion of the device inventory credentials prompt. There is a notification by the bell icon widget containing a link to this page. On this page, you can select the credentials to use out of pre-existing ones or add entirely new credentials to the system.
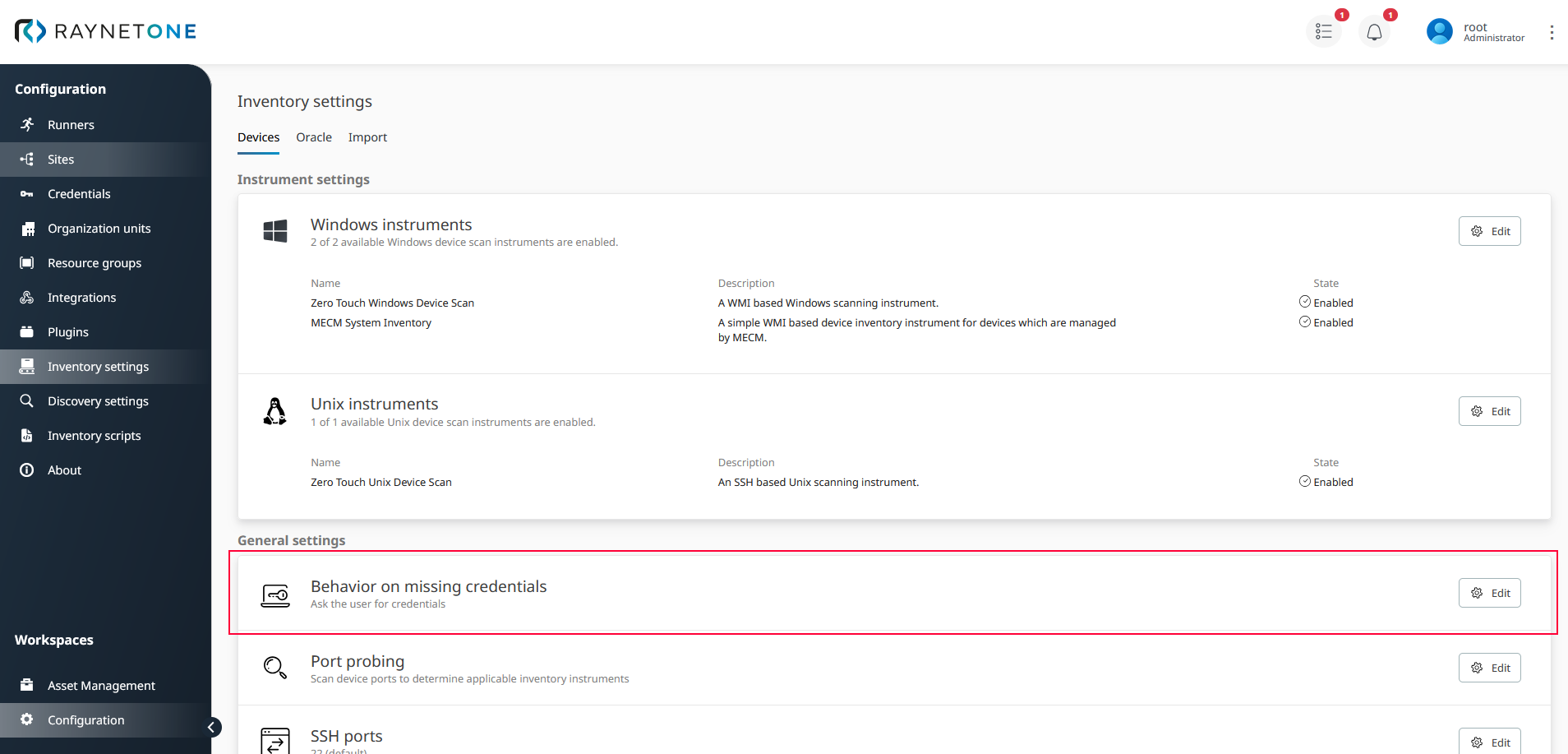
Change the logic behind the event of missing credentials by adjusting the configuration displayed above. If you don't want device inventory processes to stop in this event, you can simply turn off the user prompt for credentials entirely.
Credentials access level
The system assumes that all added credentials have the same access level to the devices they apply to. Any authenticatable credentials are selected for device inventory. No reconnection using other credentials with greater permissions or prioritization according to access level is performed.