The Vulnerabilities sub-tab will only be available if vulnerabilities for software installed on the device have been identified.
|
Be aware: In order to get the vulnerability information, a working Catalog integration is needed. Information on how to setup the Catalog integration can be found here. |
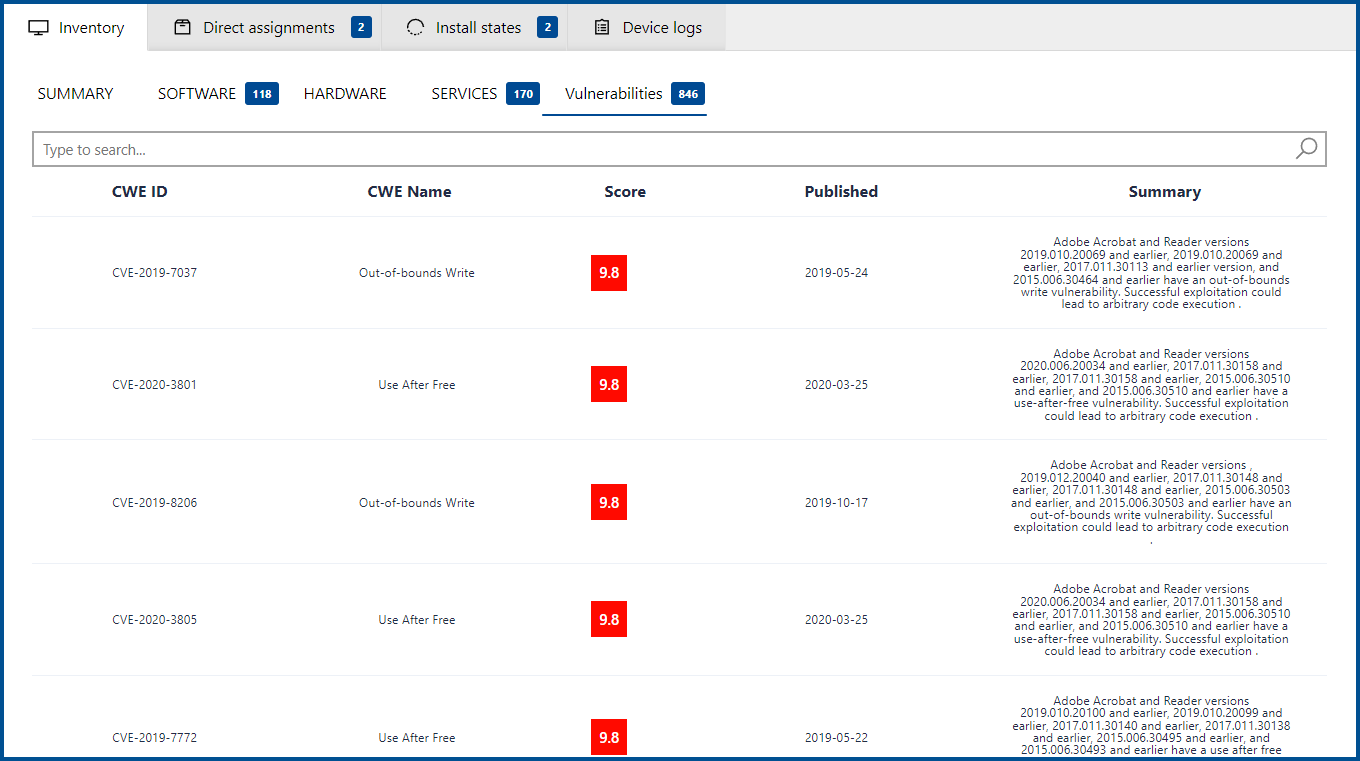
The vulnerabilities shown are sorted by their vulnerability score, showing the vulnerabilities with the highest impact first and those with the lowest impact last. The following information will be shown for each vulnerability:
•CWE ID: The ID that is used for the vulnerability in the Common Weakness Enumeration (CWE) List.
•CWE Name: The name that is used for the vulnerability in the Common Weakness Enumeration (CWE) List.
•Score: The score defining the impact of the vulnerability.
•Published: The date when the information about the vulnerability was published.
•Summary: General information about the vulnerability such as the affected software versions and a short description of the vulnerability and the risks it poses.